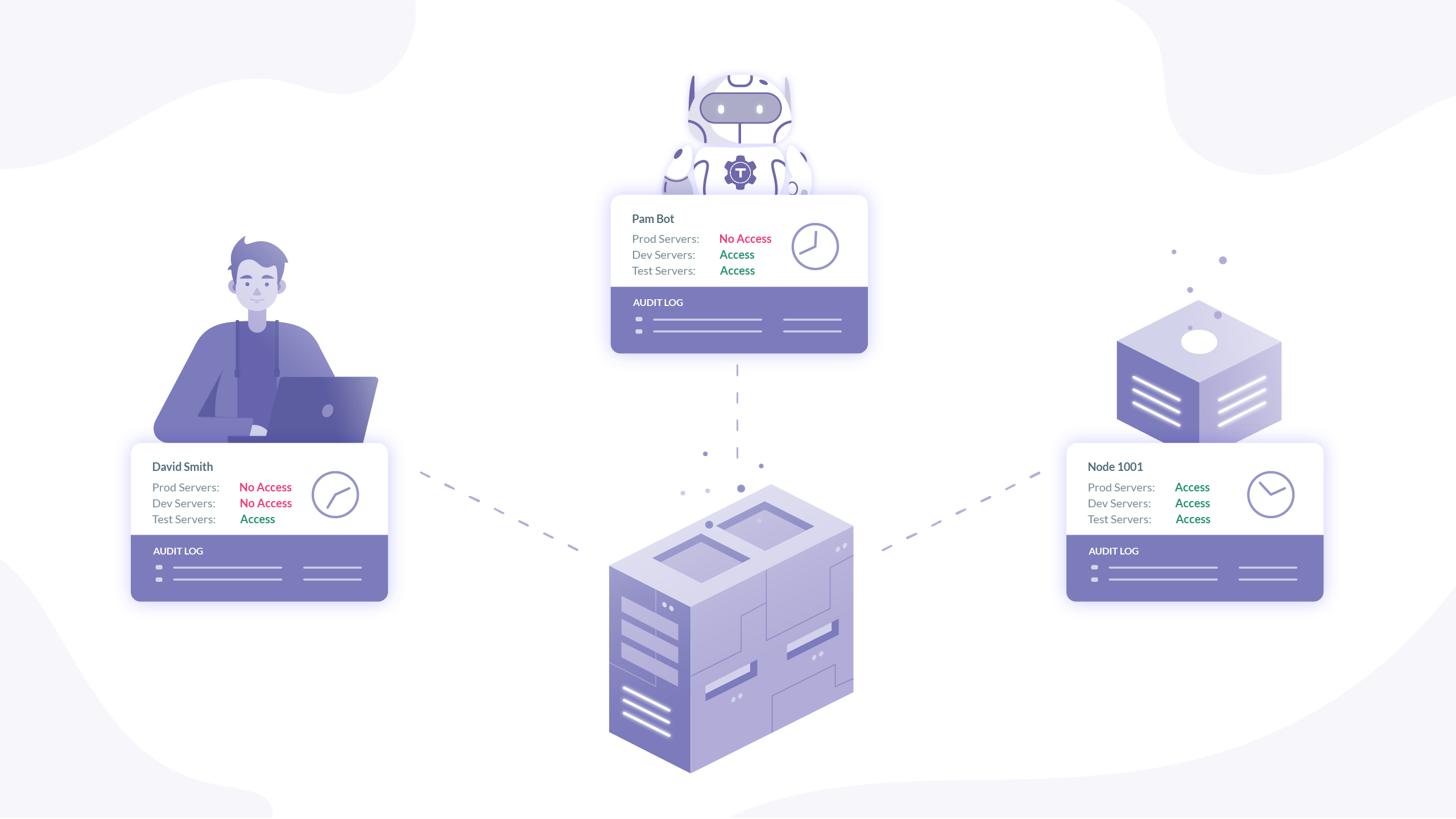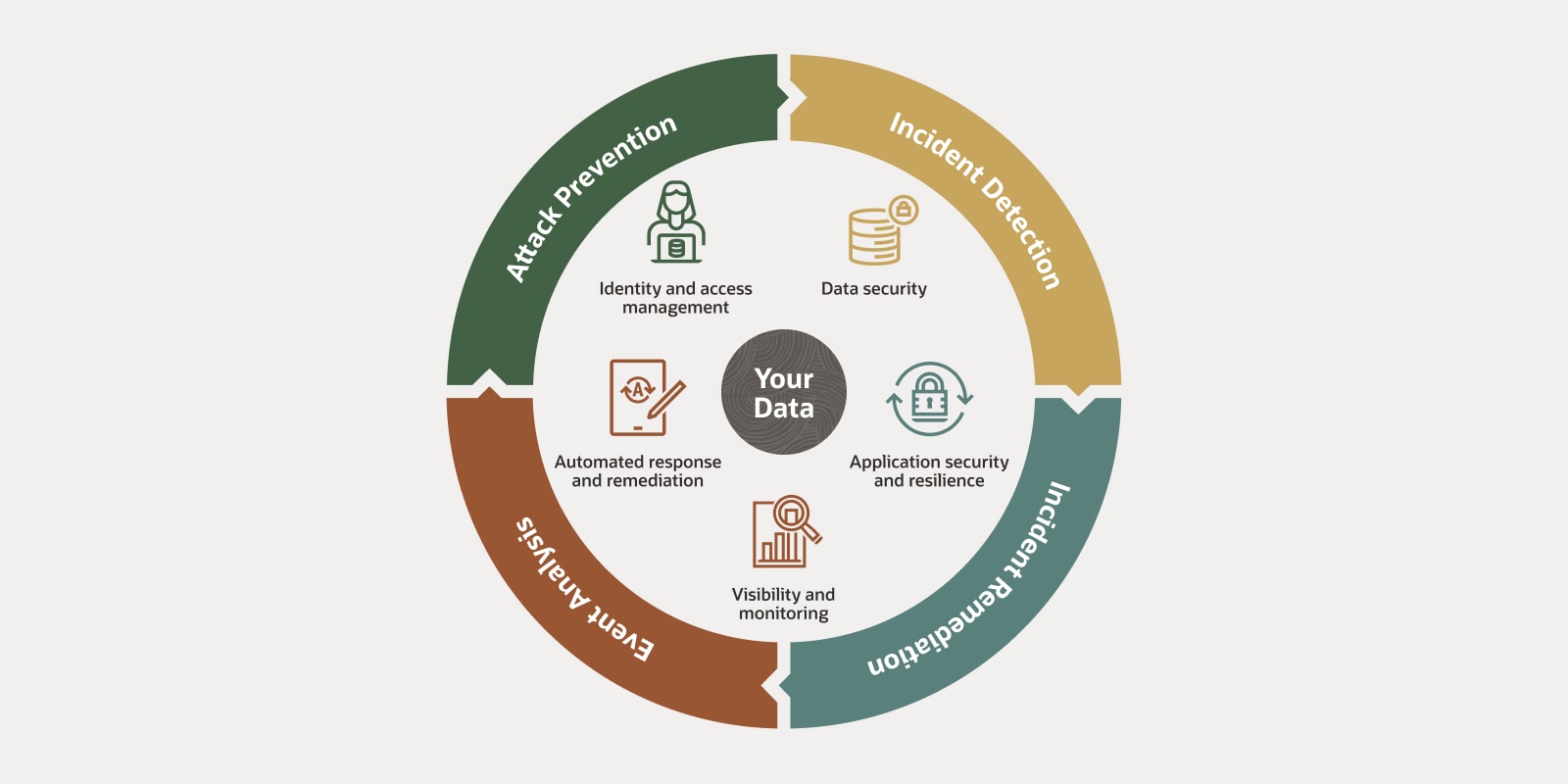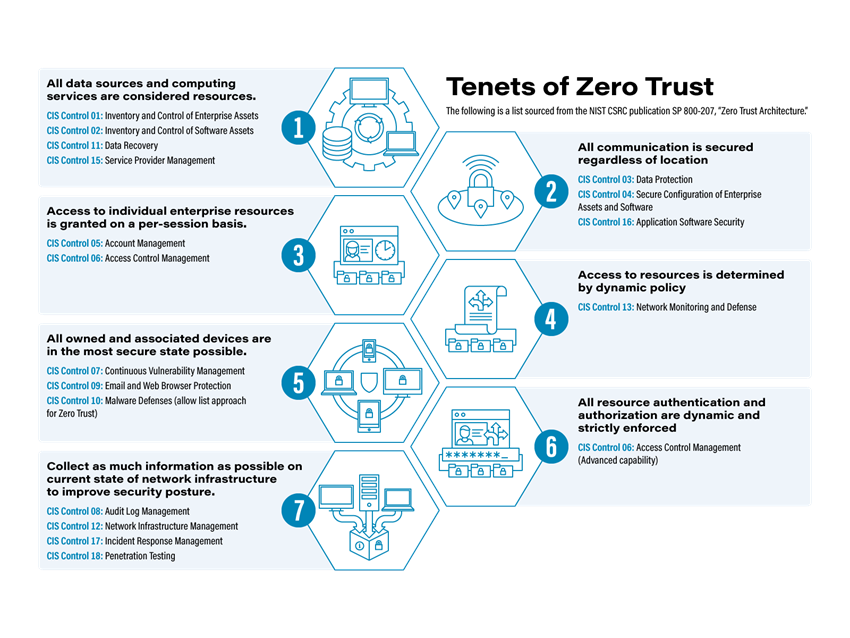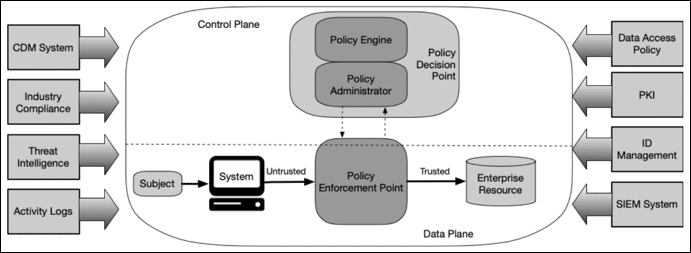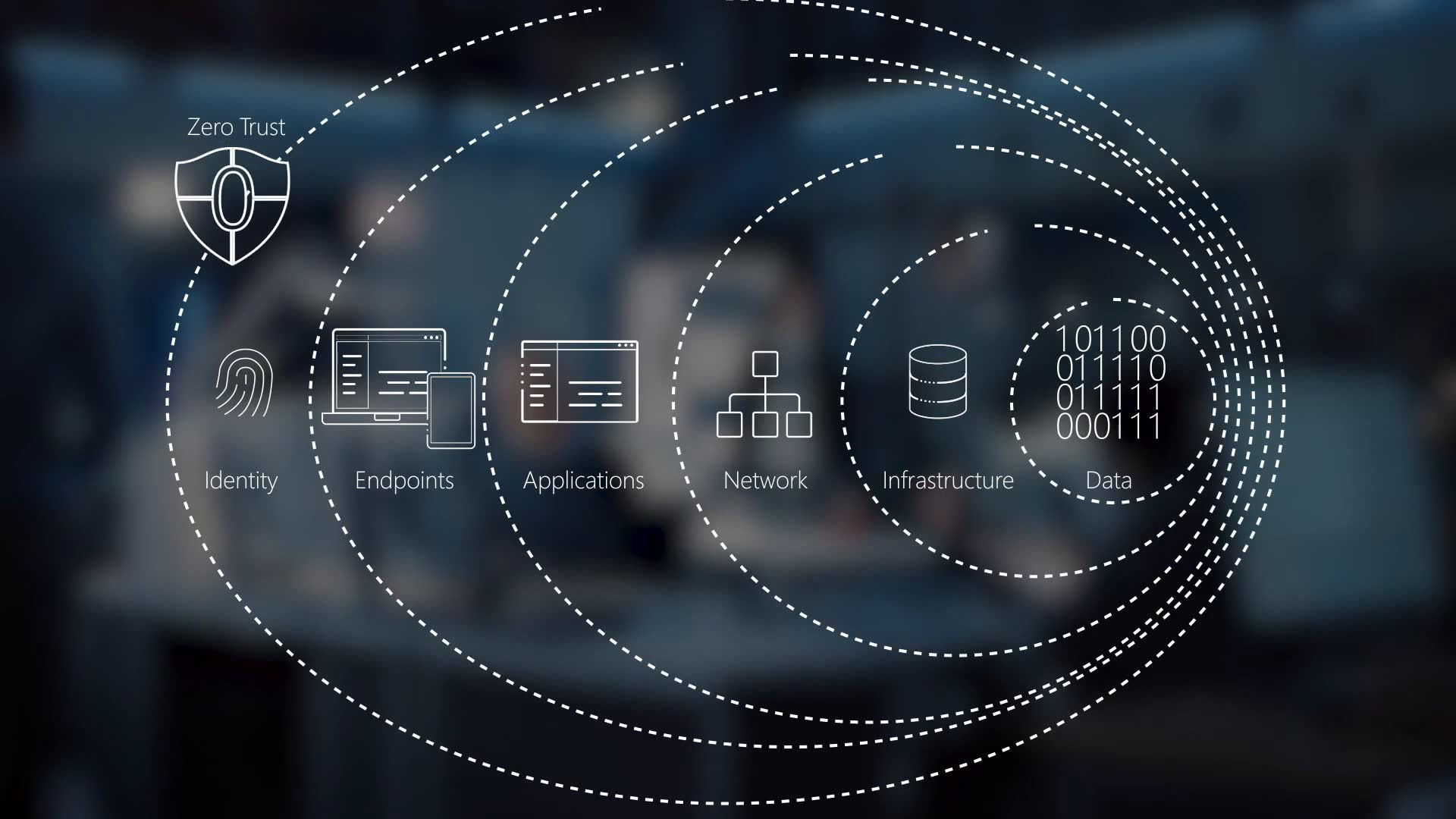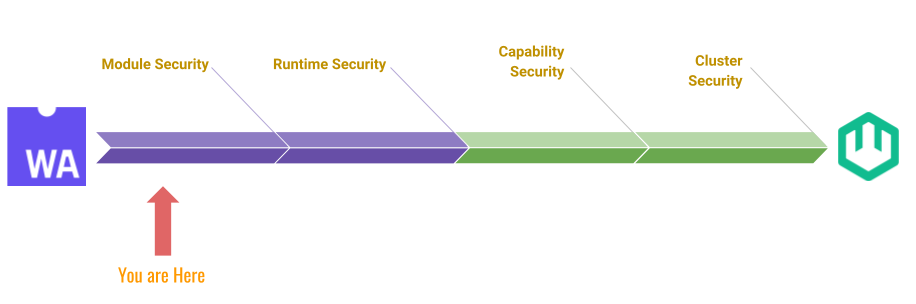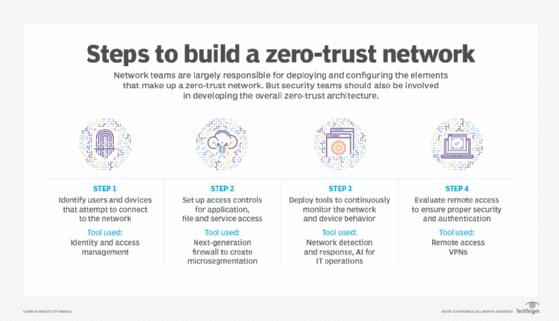
Zero-trust architecture may hold the answer to cybersecurity insider threats | MIT News | Massachusetts Institute of Technology

Cloud Computing Security Zero Trust Policy And Why You Should Embrace It | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

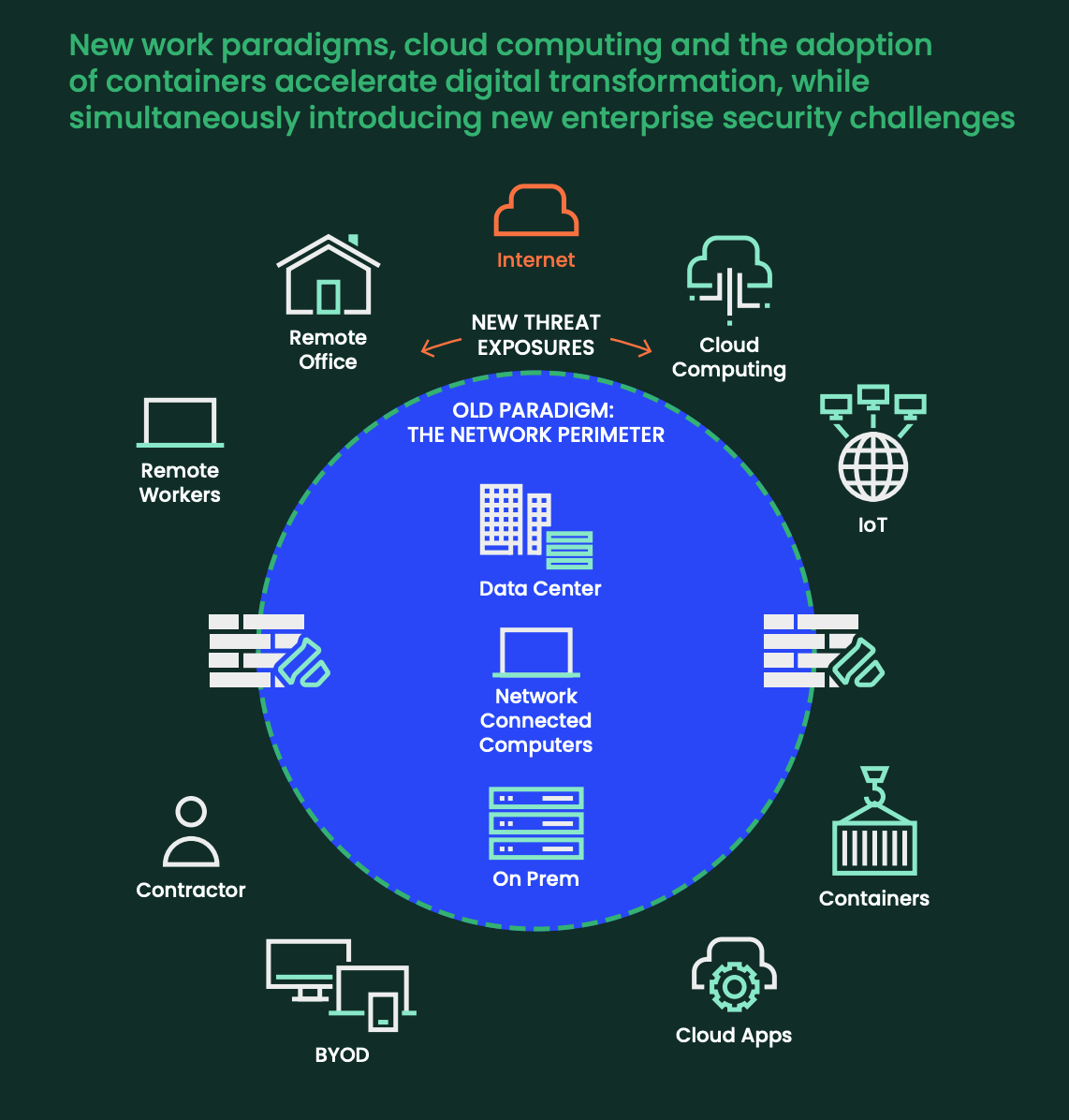
What is Zero Trust and how does it work? - ZNetLive Blog - A Guide to Domains, Web Hosting & Cloud Computing