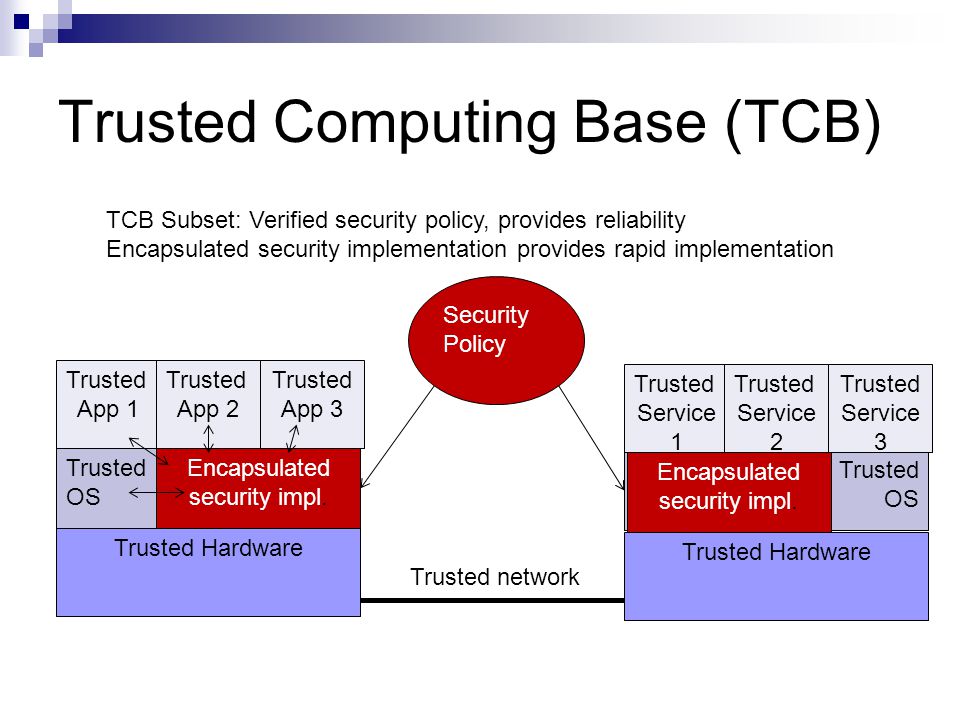
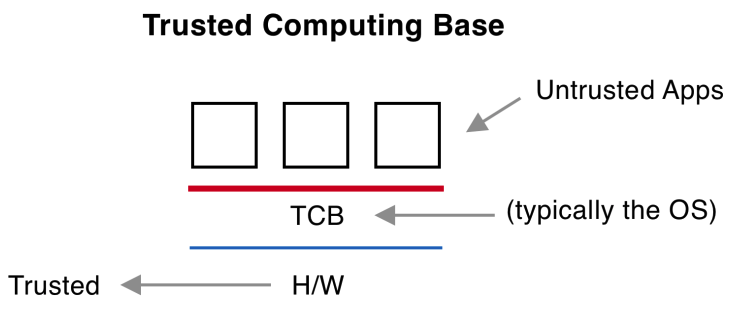
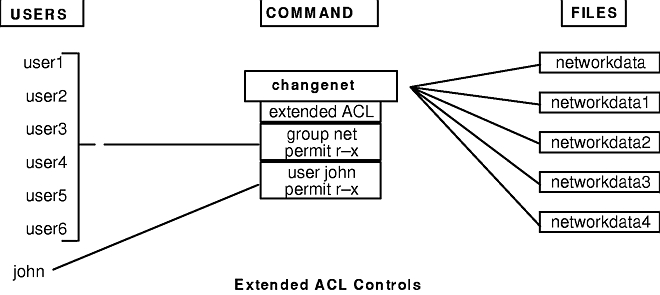
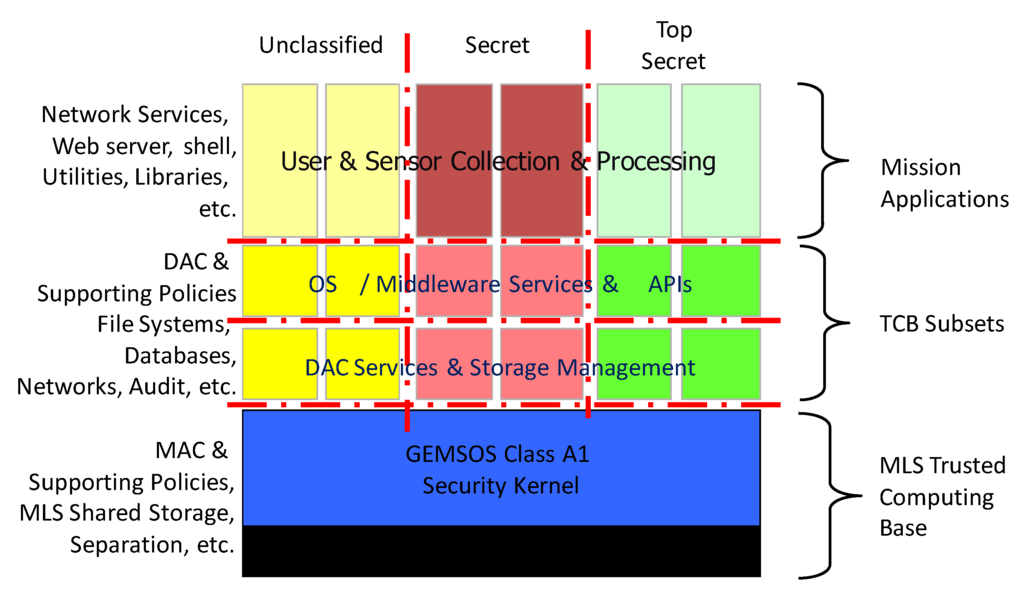
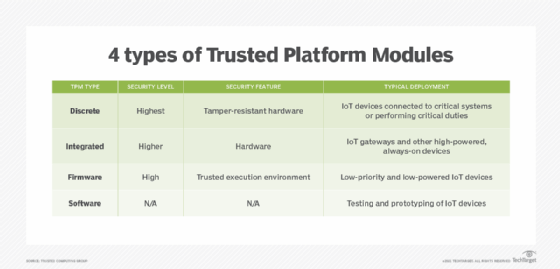
CISSP PRACTICE QUESTIONS – 20210125 by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu
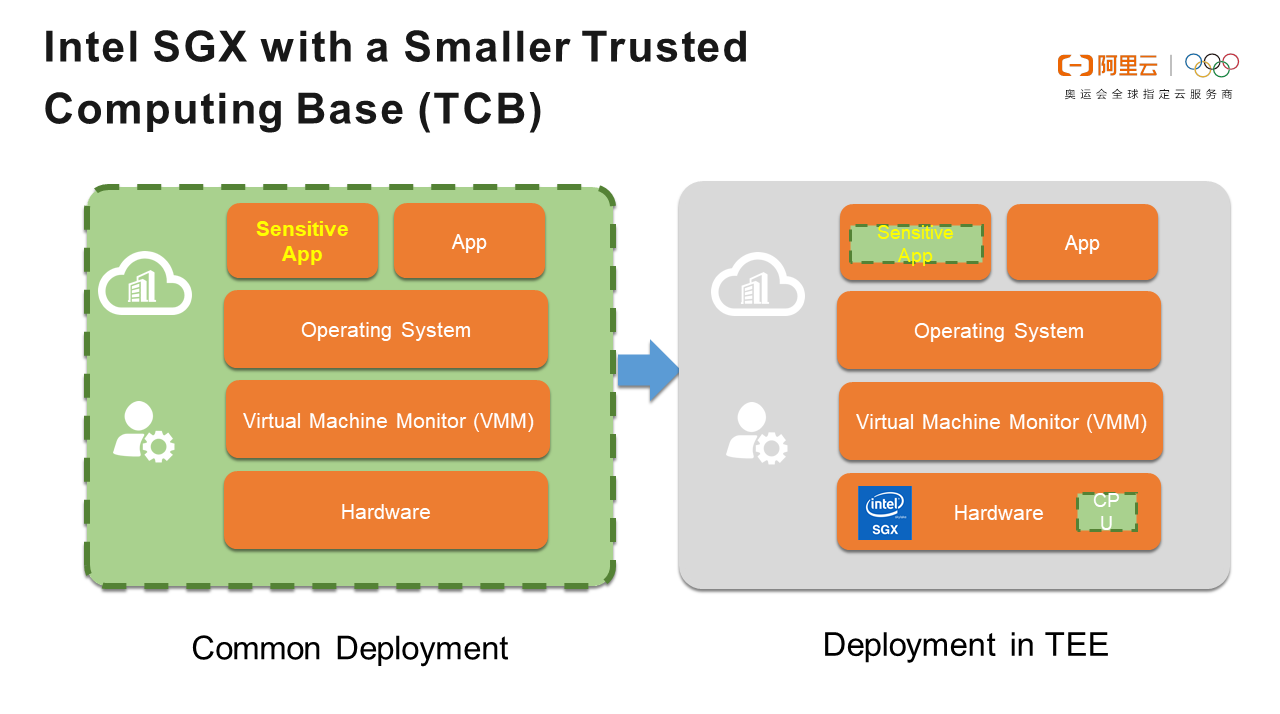
When Kubernetes Encounters Confidential Computing, How Does Alibaba Protect the Data in the Container? - Alibaba Cloud Community
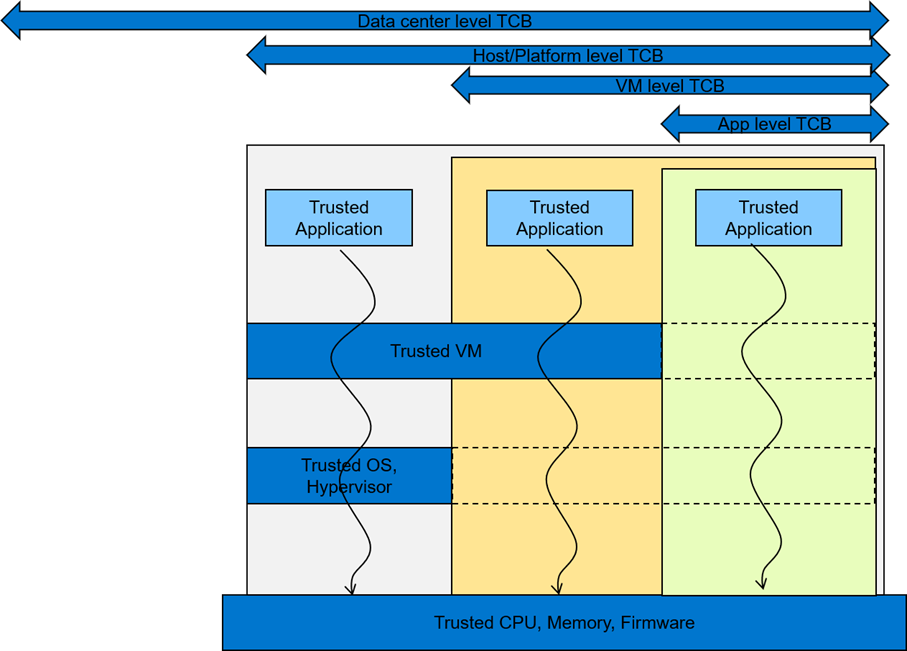
Understanding Confidential Computing with Trusted Execution Environments and Trusted Computing Base models | Dell Technologies Info Hub
![PDF] Integrating a Trusted Computing Base Extension Server and Secure Session Server into the LINUX Operating System | Semantic Scholar PDF] Integrating a Trusted Computing Base Extension Server and Secure Session Server into the LINUX Operating System | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b426ea6d312fd9671e23f3e8826701a26783f4c4/34-Figure2-1-1.png)
PDF] Integrating a Trusted Computing Base Extension Server and Secure Session Server into the LINUX Operating System | Semantic Scholar

Security Architecture | CISSP Exam Cram: Security Architecture and Models | Pearson IT Certification