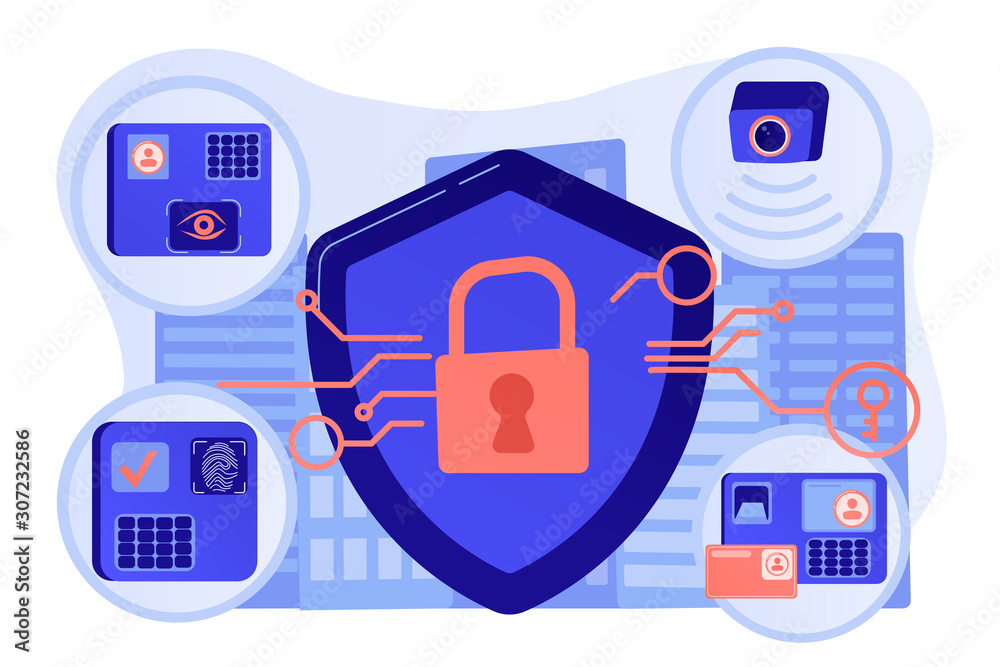
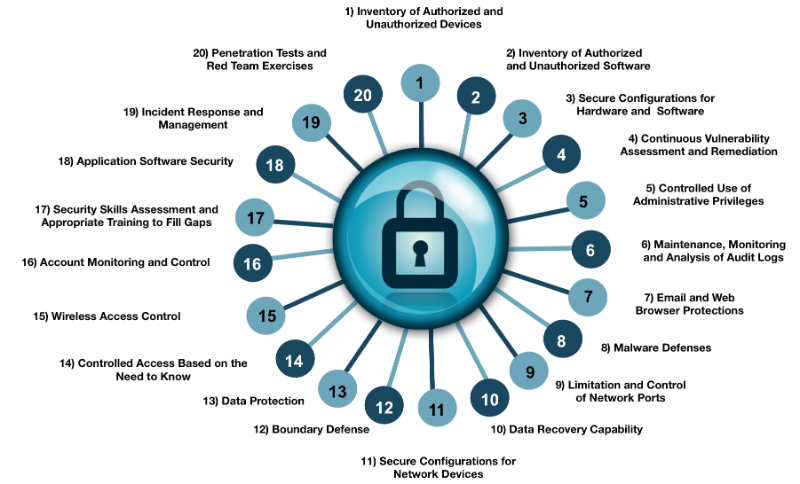
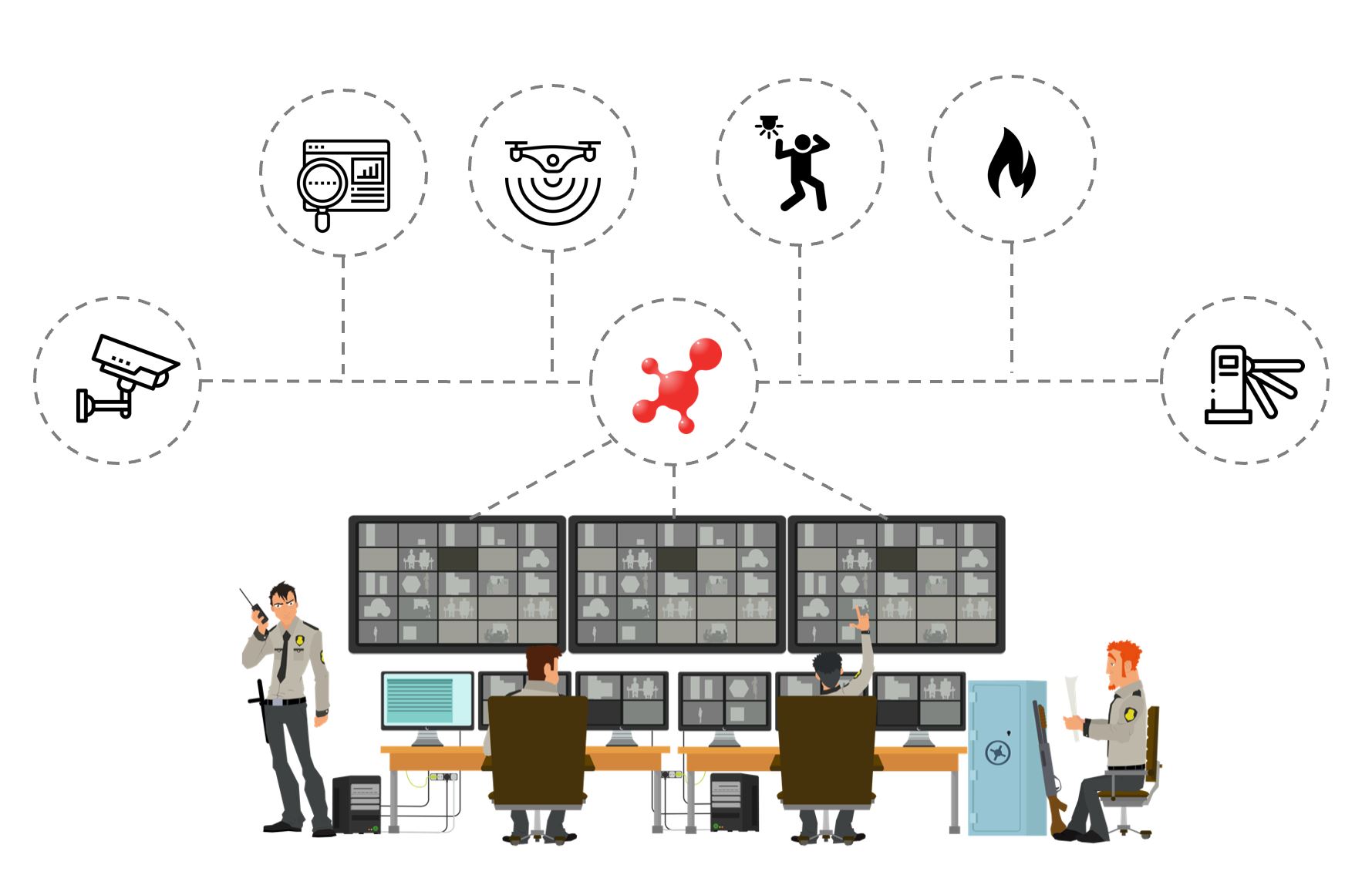
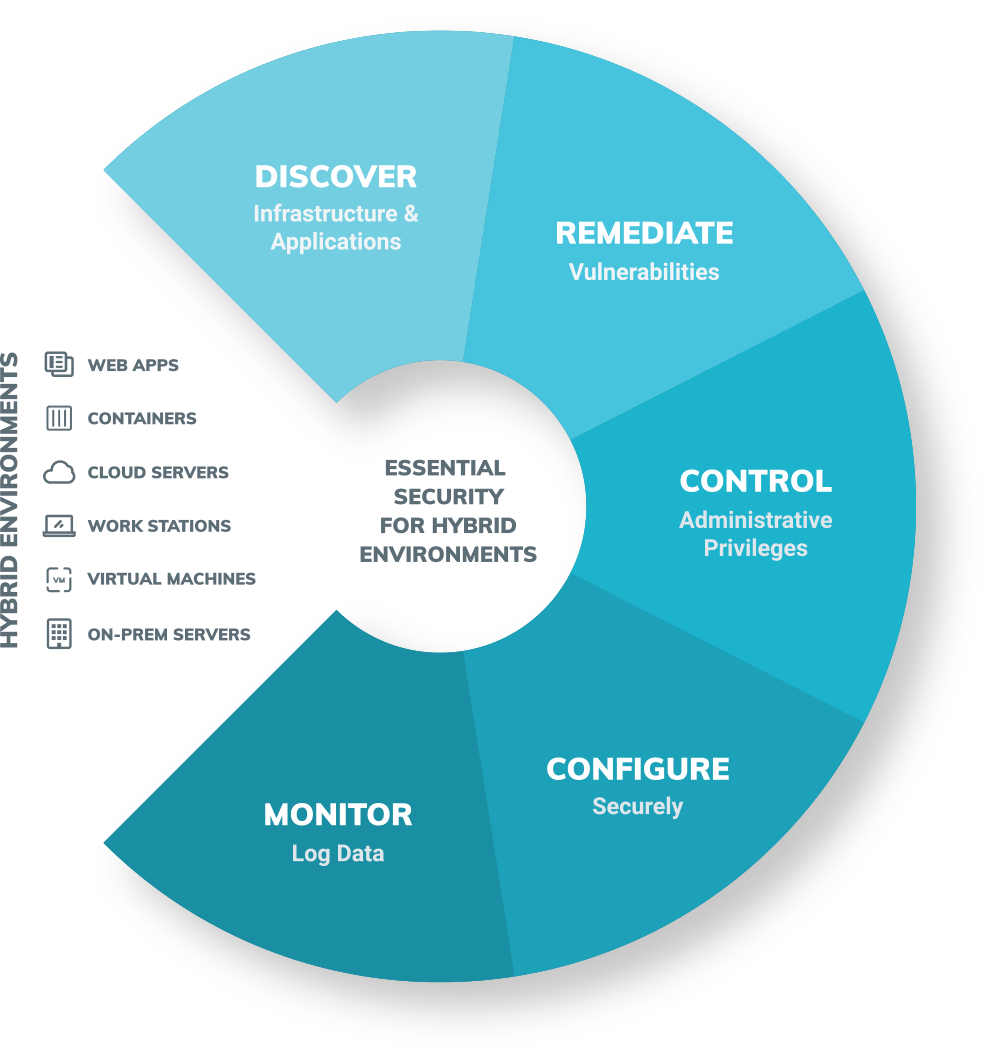
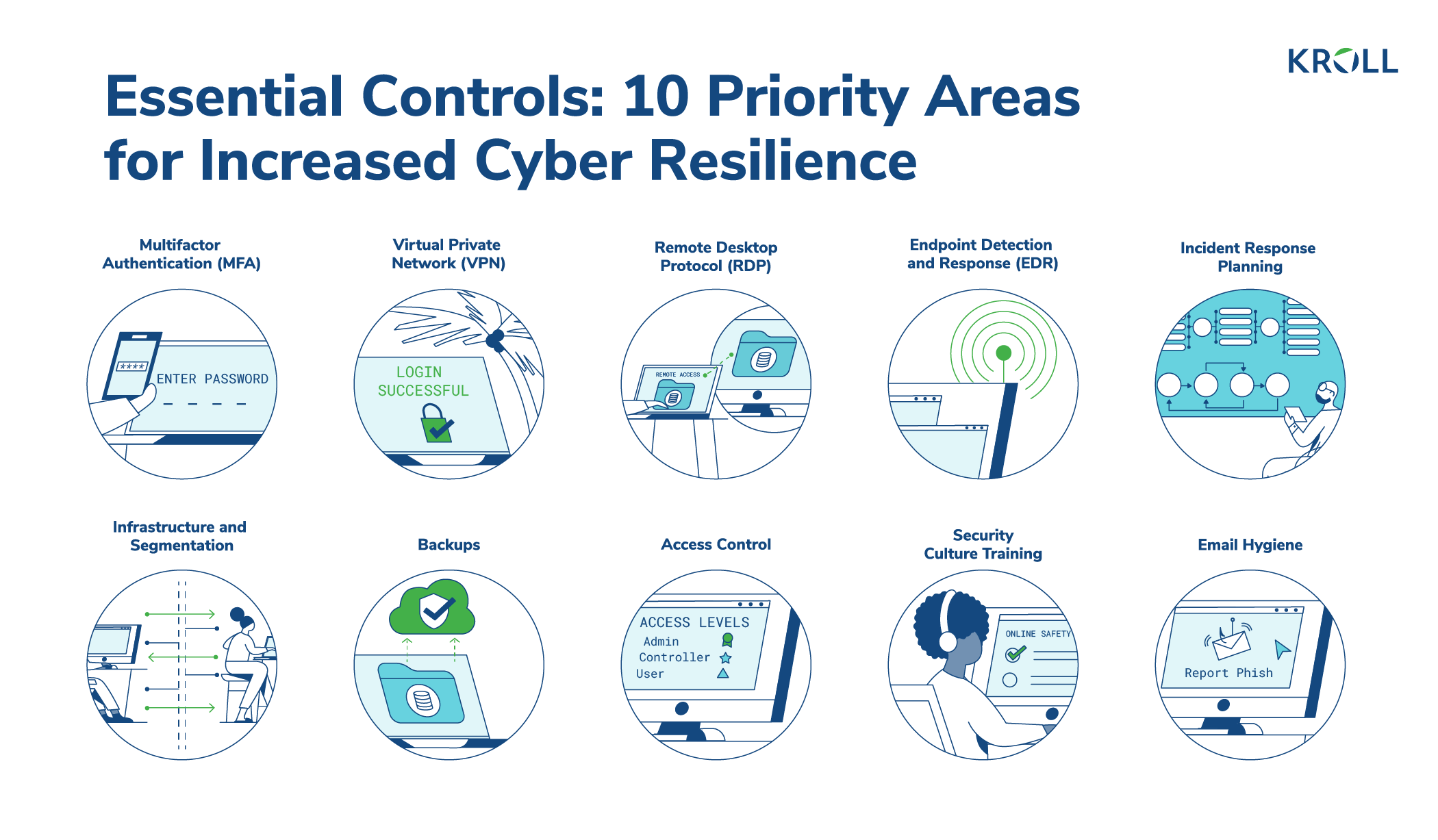
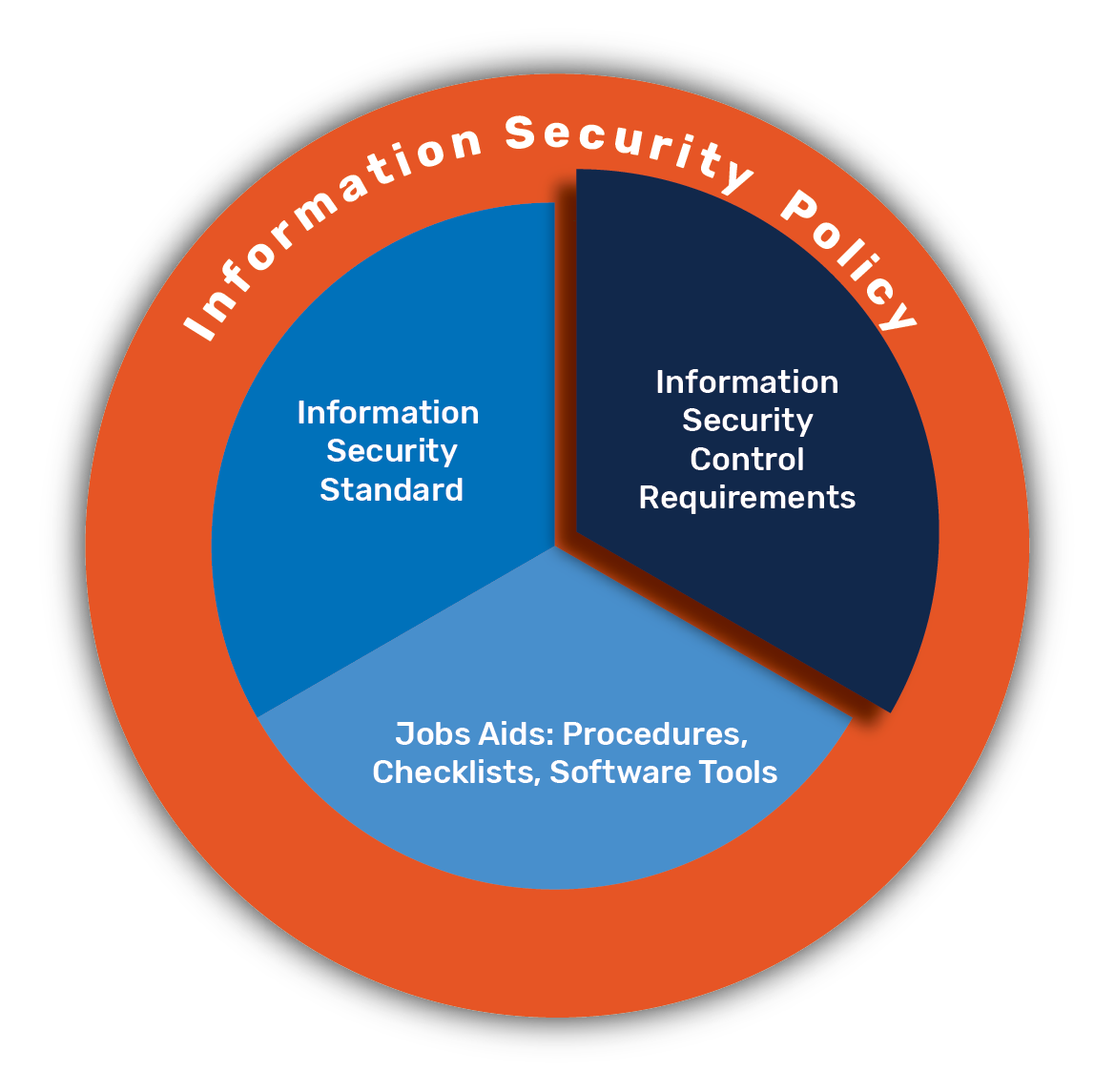
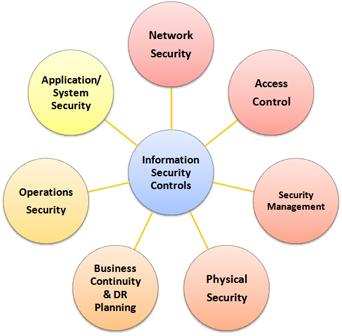
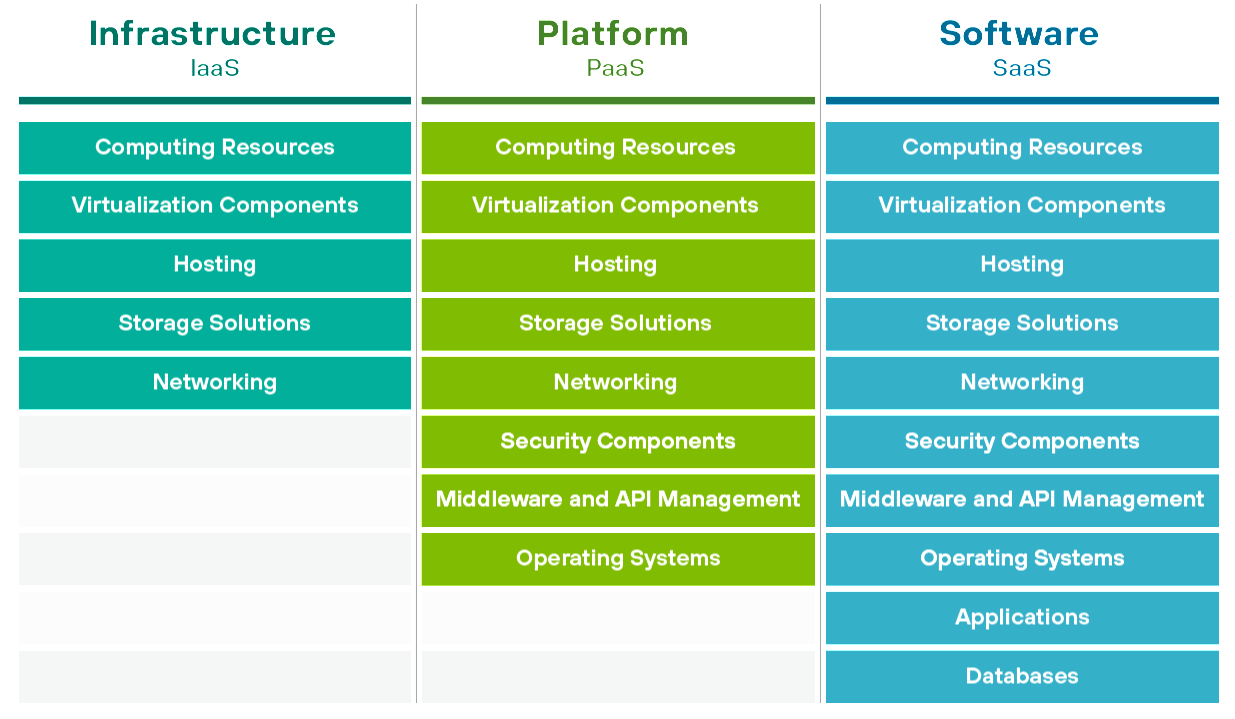
Primary Considerations and Pitfalls for Security Control Room Design | 2018-09-11 | Security Magazine

Computer Applications for Security, Control and System Engineering (kartoniertes Buch) | Buchhandlung am Markt

Industry 4.0 Modern Factory: Security Control Room with Multipoke Computer Screens Showing Surveillance Camera Footage Feed. High-Tech Security Stock-Foto | Adobe Stock