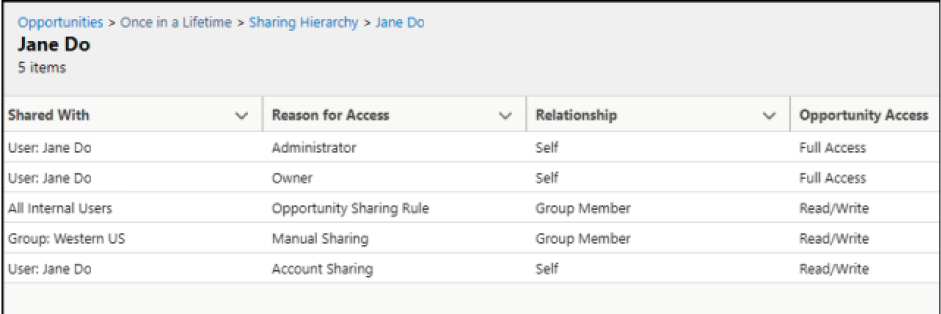
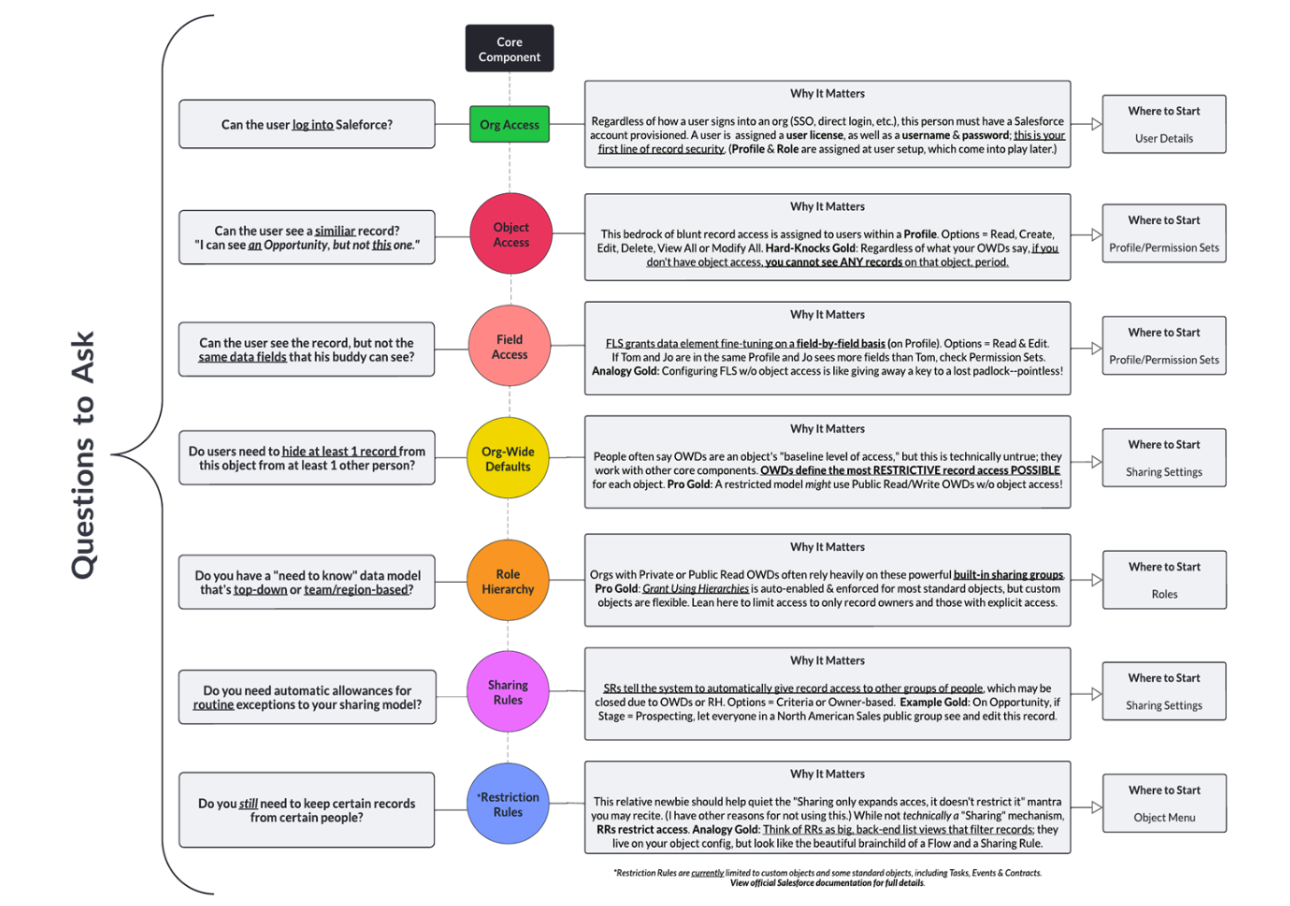
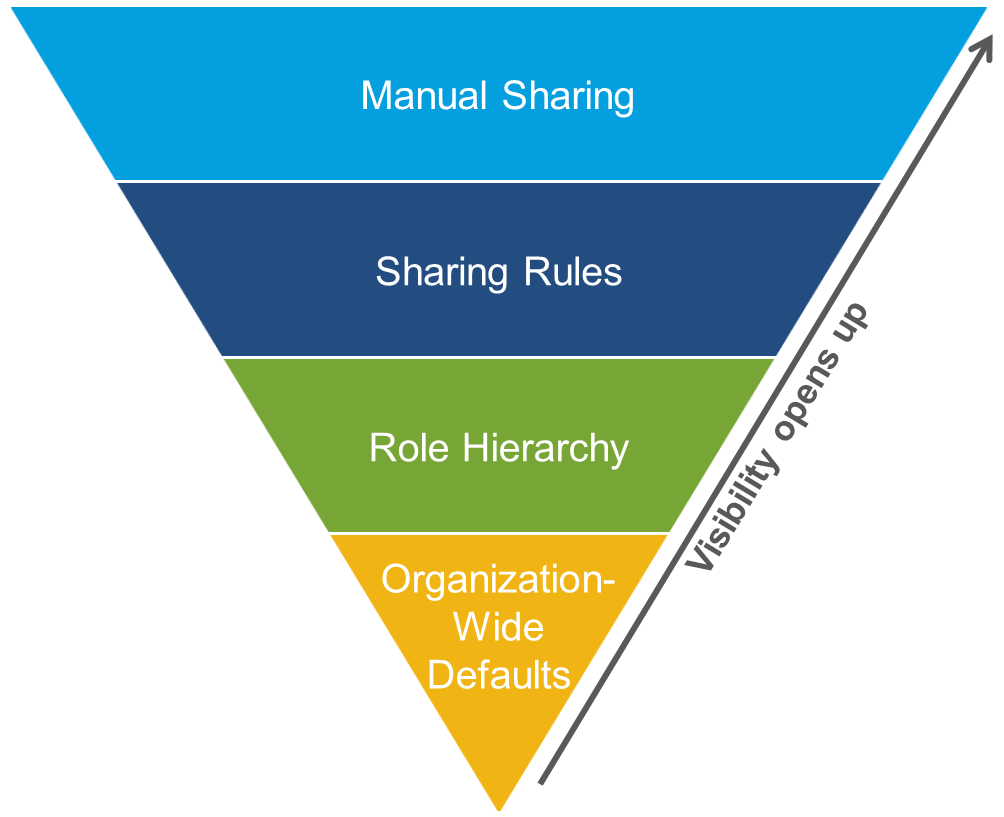
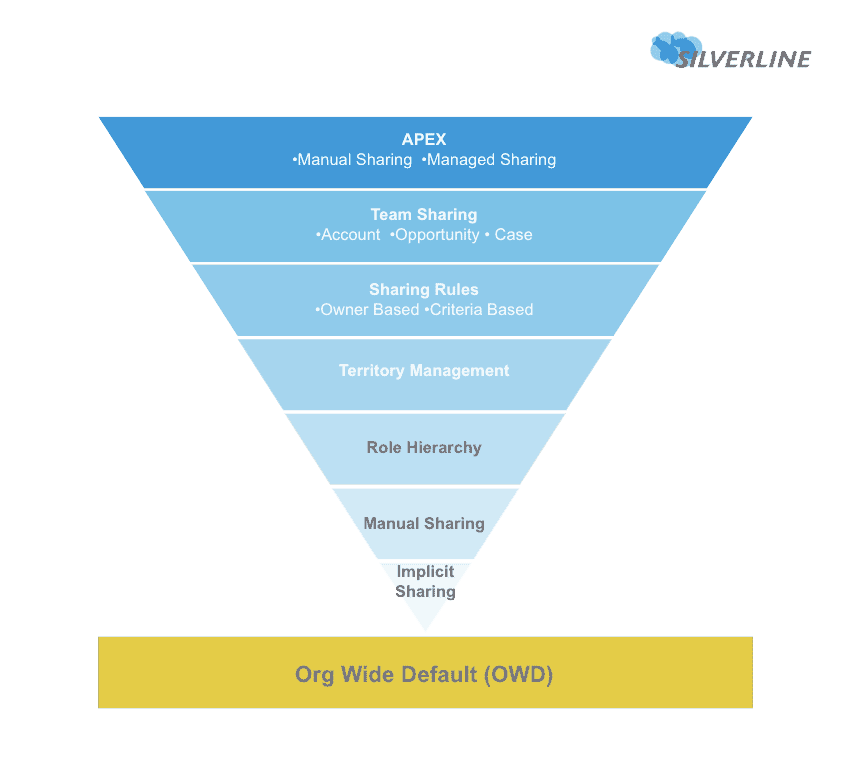
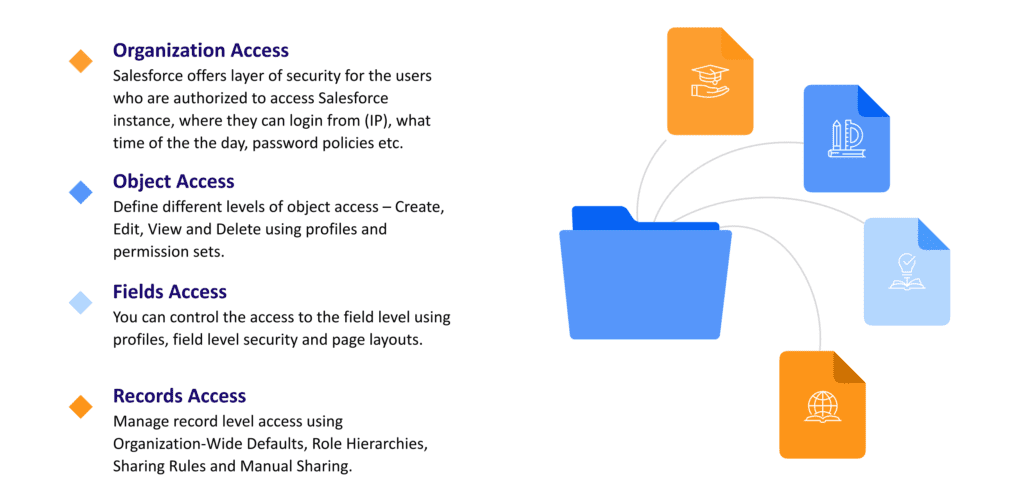
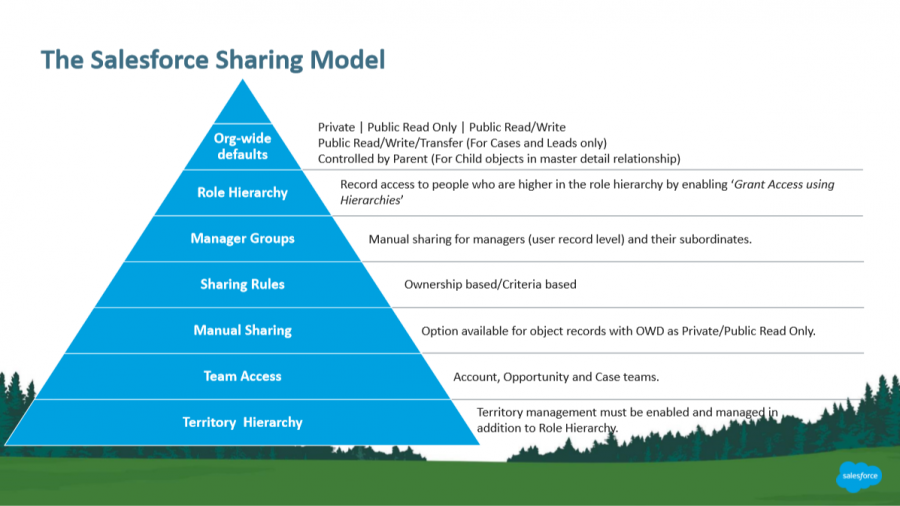
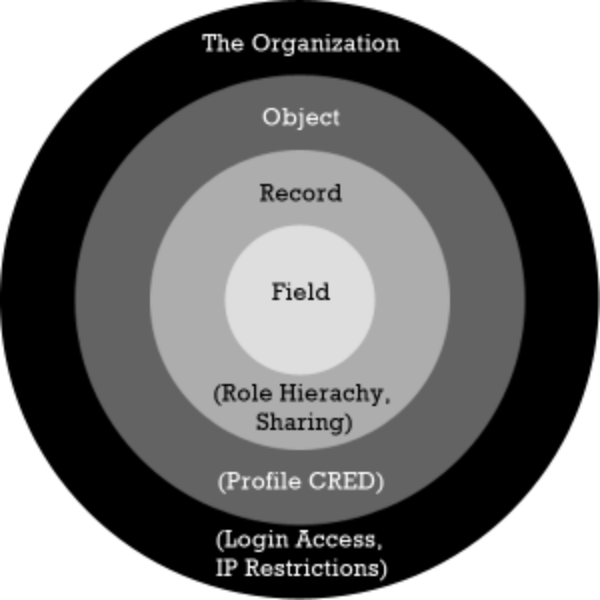
Expert Corner: Manage Record Access and Visibility in Salesforce with Product Manager Larry Tung - Salesforce Admins

Salesforce Security Sharing Model or the layer of visibility | Knowledge comes from experience and continuous practical hands-on ...