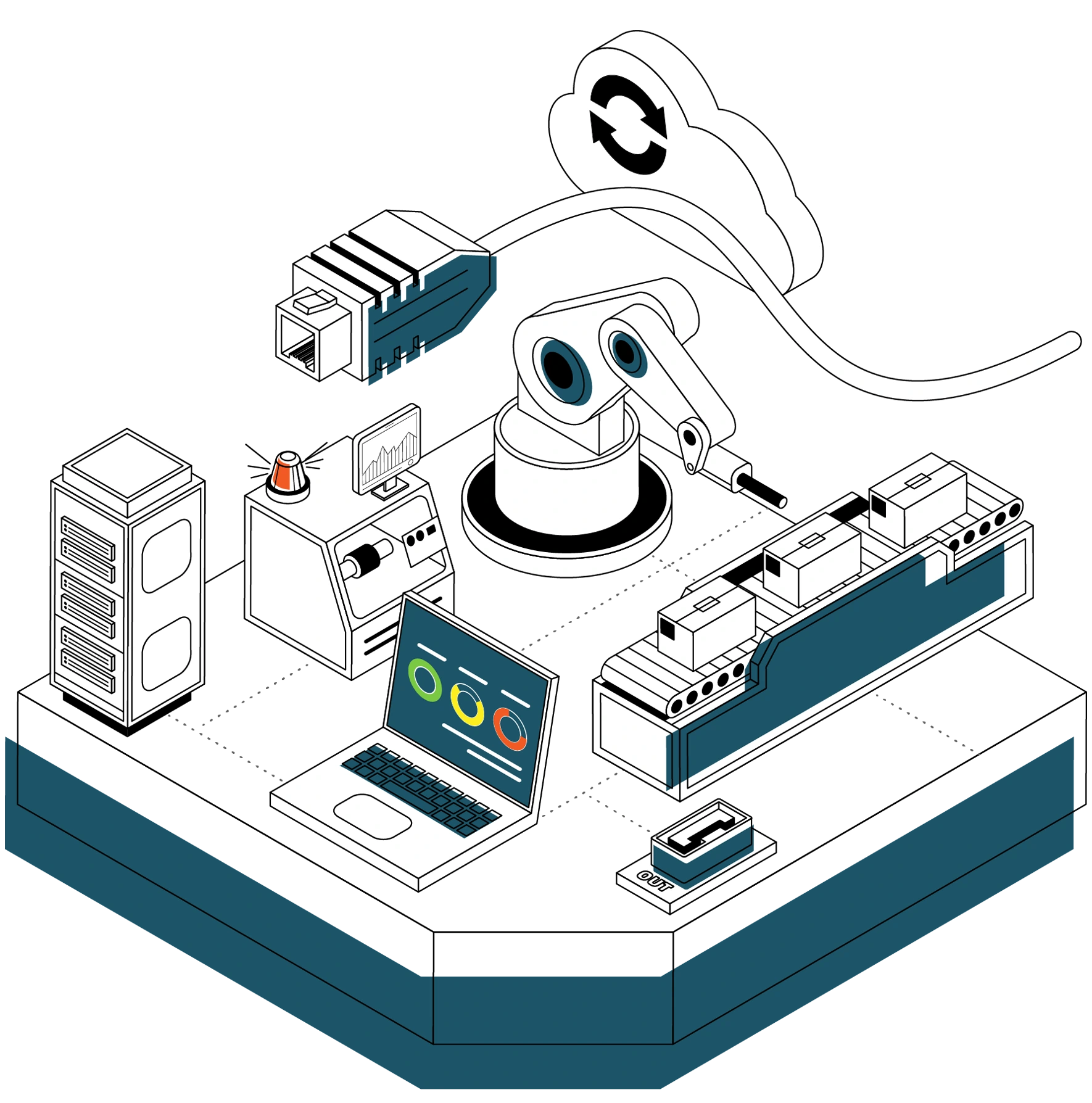
Set of linear icons computer and ot. Stock vector illustration of a set of linear icons computer and other electronic | CanStock

OT-Security – Wie sich mittelständische Industrieunternehmen gegen Cyberangriffe wappnen können, TÜV Rheinland, Pressemitteilung - PresseBox












%20(1)-1.jpeg?width=600&name=AdobeStock_254487811%20(1)%20(1)-1.jpeg)