Threat Hunting Workshop: Hands-On, Real-World Dynamic Attack Labs – October 1, 2020 | Networking For Future, Inc. (NFF)

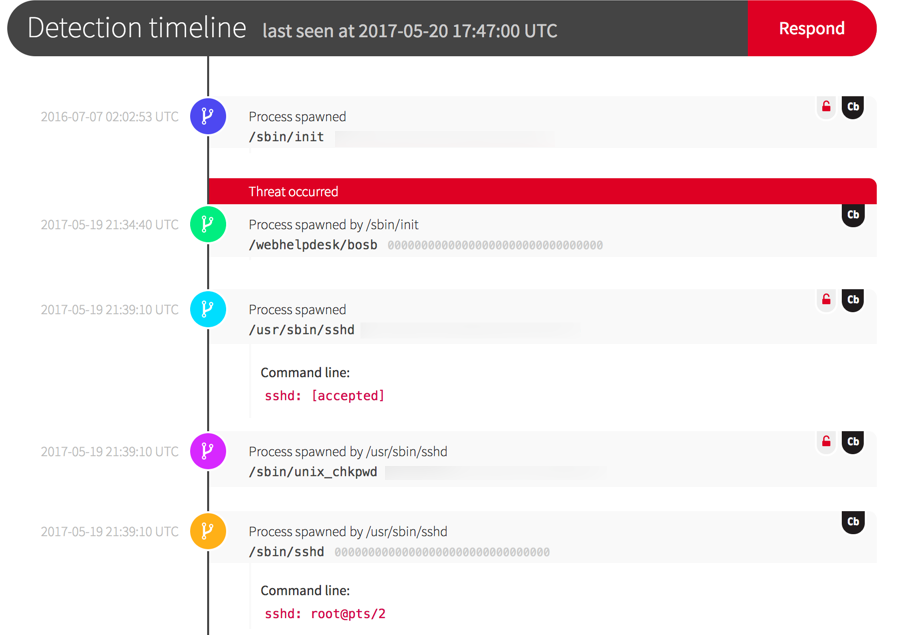
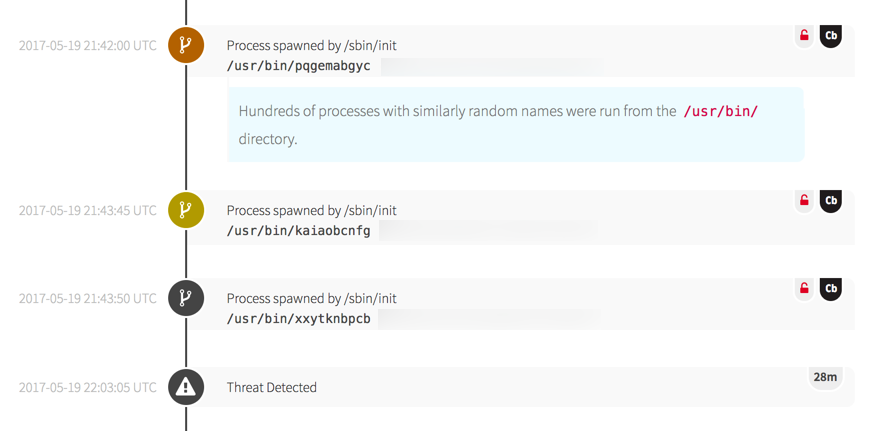
Katie Nickels on Twitter: "THIS IS THE MEATY STUFF. HANDS ON KEYBOARD ATTACK. Fewer victims got this far from public reporting. Renamed adfind could be a good hunt/detection opportunity. Hunt for/detect on

Premium Photo | Close-up image of man planning hacker attack. man using laptop, typing code. male hands on keyboard. hacking, technology, cybercrime concept
Deconstructing the Solarwinds Supply Chain Attack and Deterring it: Honing in on the Golden SAML Attack Technique

Typing on a computer keyboard - concept cybersecurity, phishing, hacking, social engineering attack, dark web, viruses and trojans Stock Photo - Alamy

Hacker Typing On Laptop Keyboard Watching For Skull Hologram Screen. Cyber Crime, Online Attack, Hacking, Security Breach, Danger And Phishing Concept. Camera Moving Sideway With Writing Hands. Stock Photo, Picture And Royalty
Premium Photo | Cyberattack and internet crime hacking and malware concepts digital binary code data numbers and secure lock icons on hacker hands working with keyboard computer on dark blue tone background

Hacking / Cyber attack in progress. Hands on keyboard in a dark discreet surroun , #Affiliate, #progress, #Hands, #keyboard, #Hacking… | Cyber attack, Cyber, Attack










/cloudfront-us-east-1.images.arcpublishing.com/gray/JJZ5KSWWKBG6FILVYTIZO52EEU.jpg)