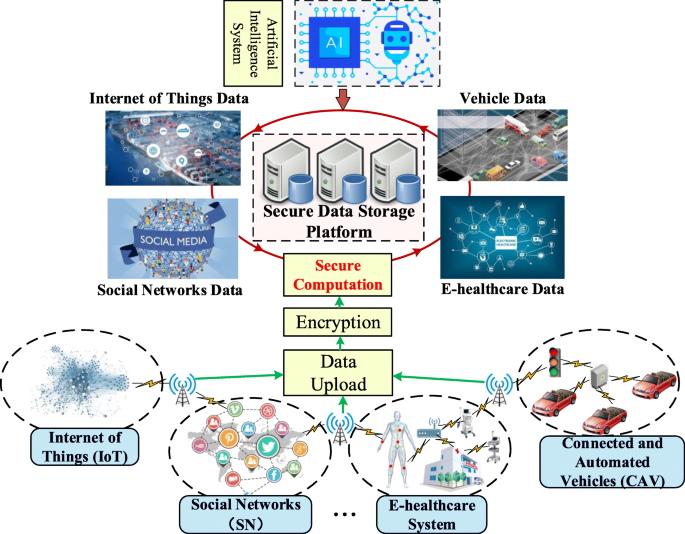
Applied Sciences | Free Full-Text | Communication-Efficient Secure Federated Statistical Tests from Multiparty Homomorphic Encryption

Buy Ramifications of Darpa's Programming Computation on Encrypted Data Program Book Online at Low Prices in India | Ramifications of Darpa's Programming Computation on Encrypted Data Program Reviews & Ratings - Amazon.in
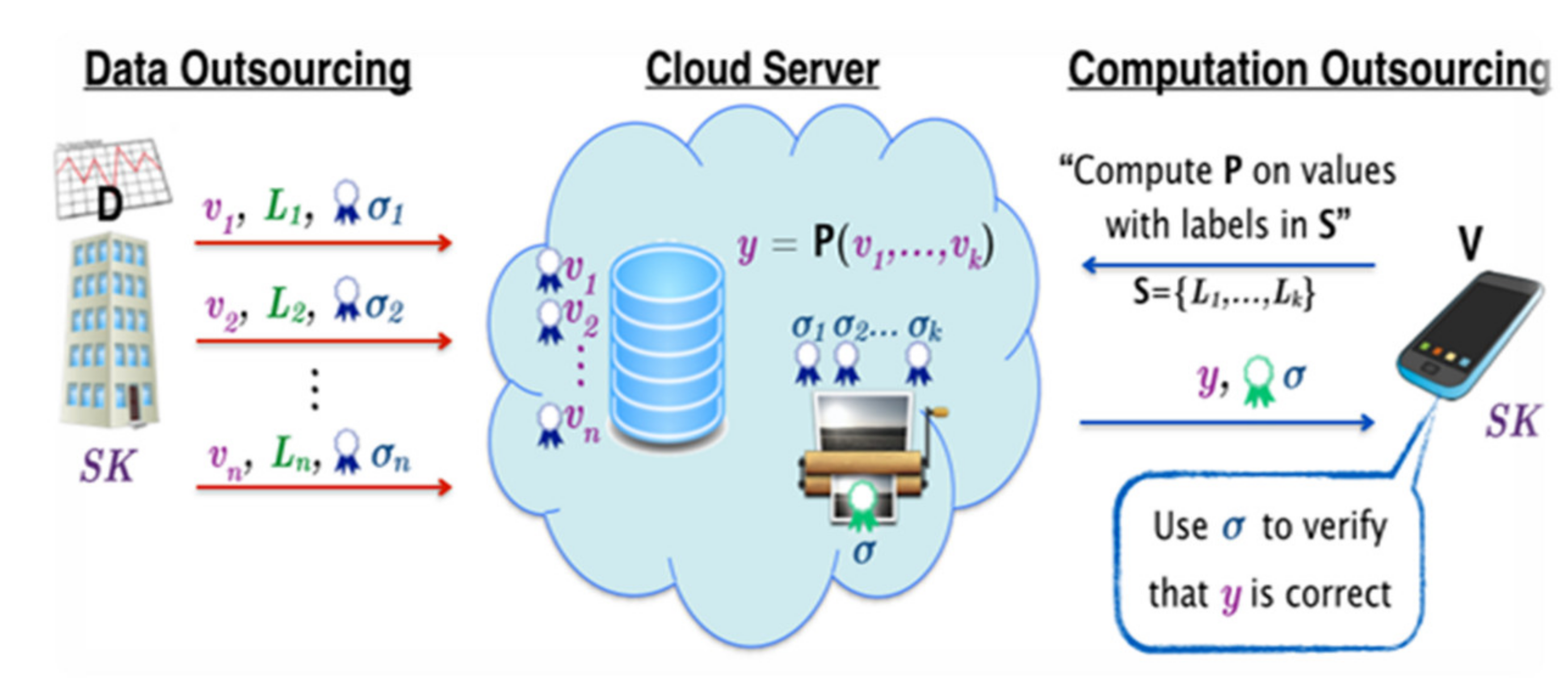
Technologies | Free Full-Text | A Verifiable Fully Homomorphic Encryption Scheme for Cloud Computing Security
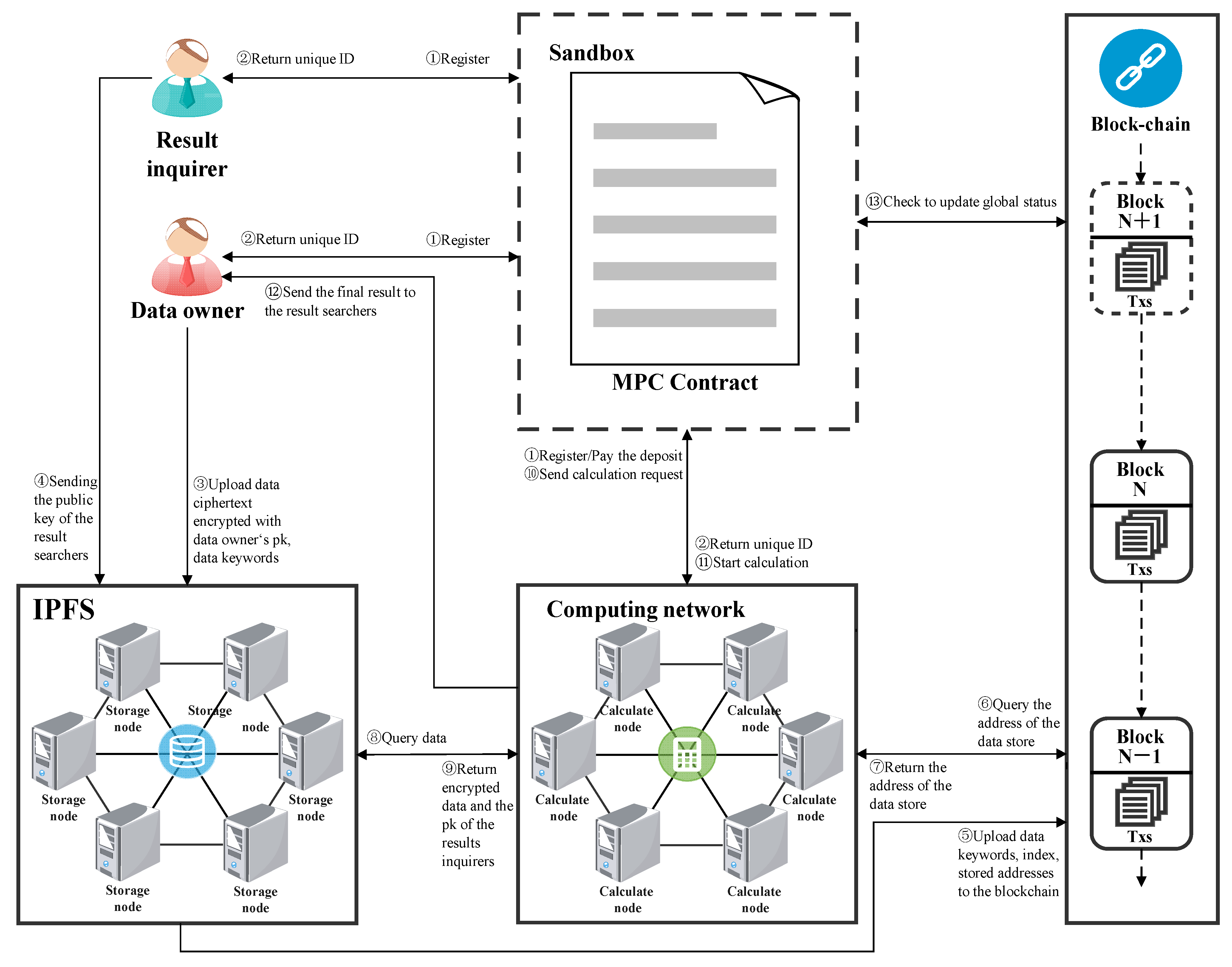
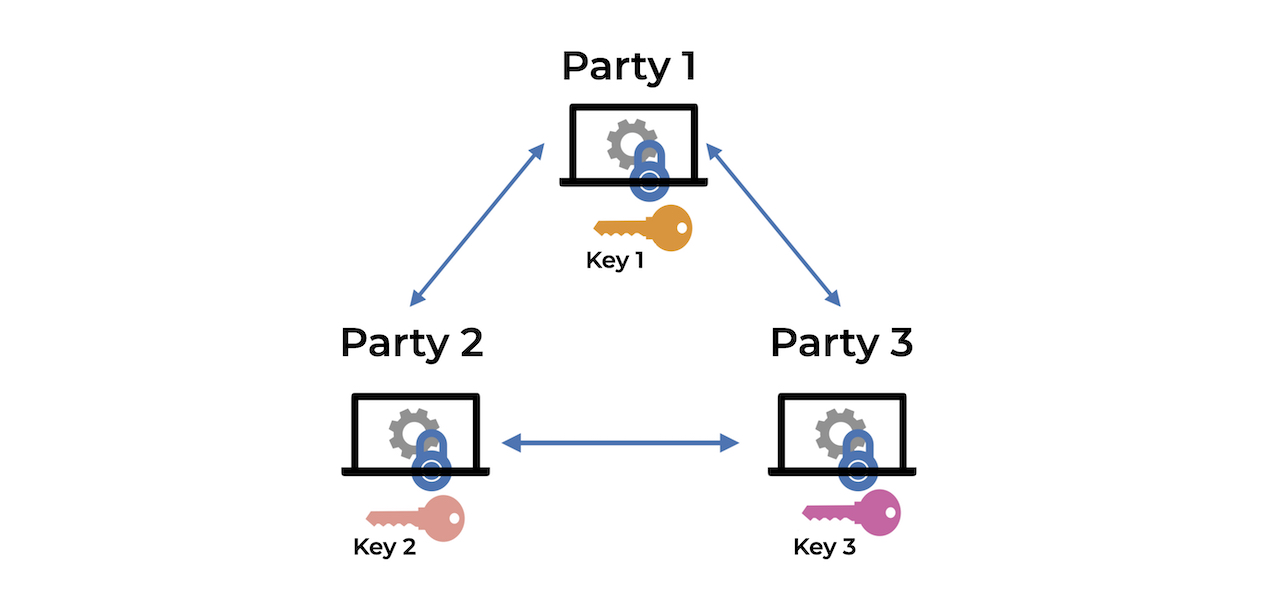
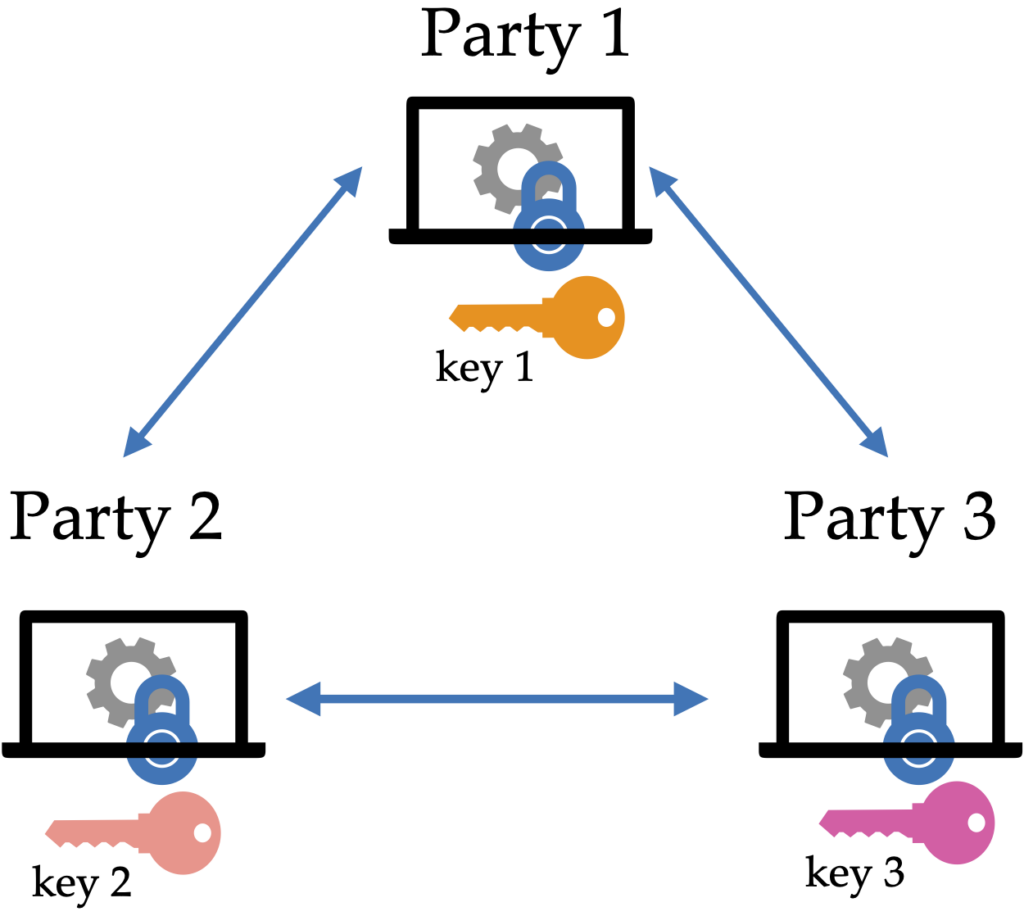
Information | Free Full-Text | A Blockchain-Based Secure Multi-Party Computation Scheme with Multi-Key Fully Homomorphic Proxy Re-Encryption
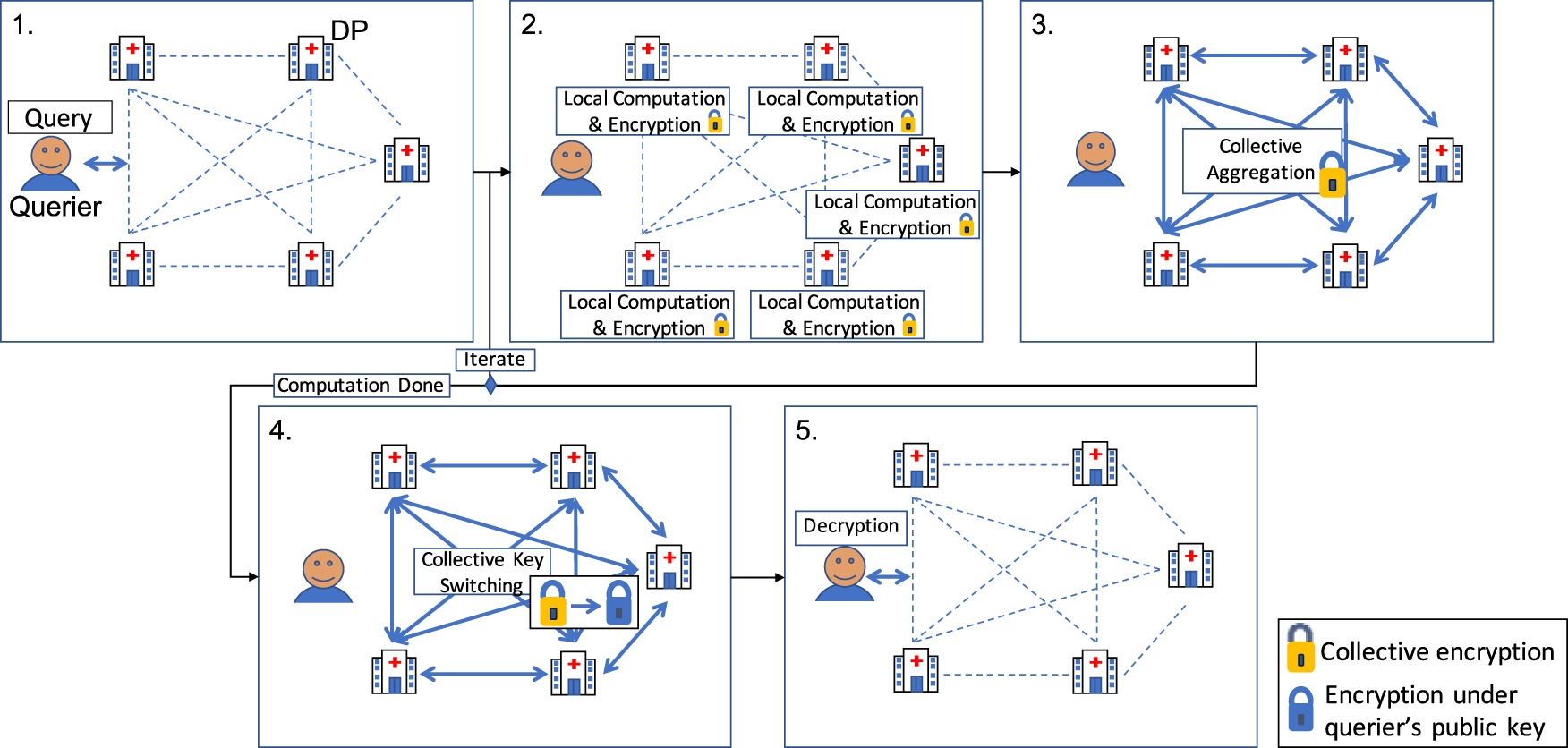
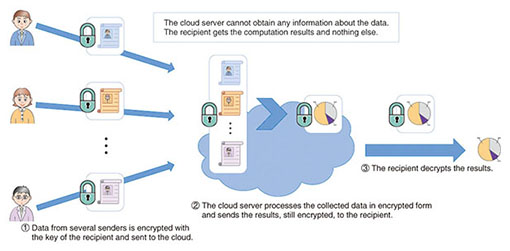
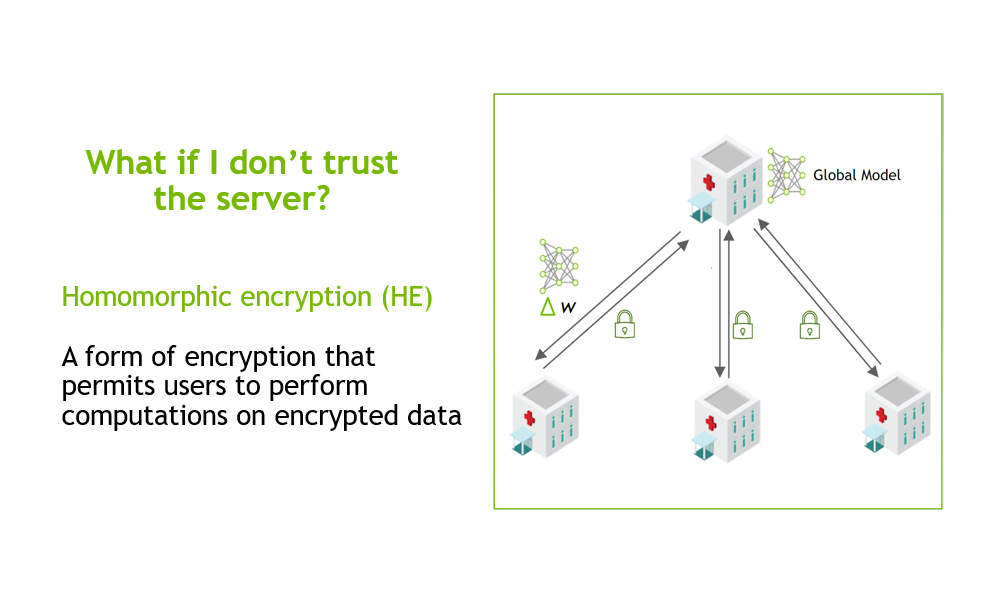
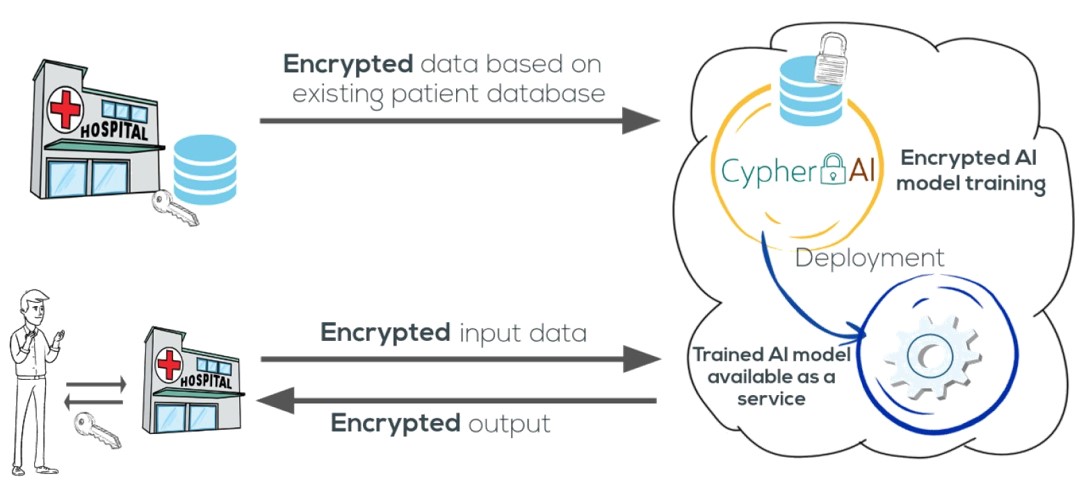
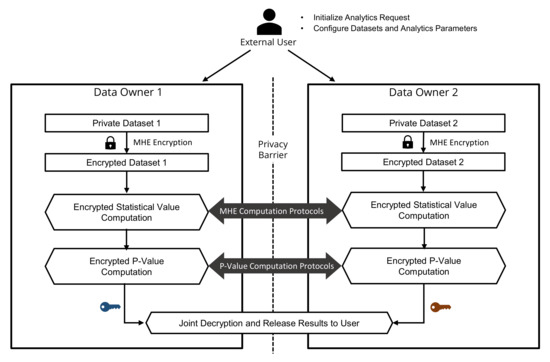
Truly privacy-preserving federated analytics for precision medicine with multiparty homomorphic encryption | Nature Communications

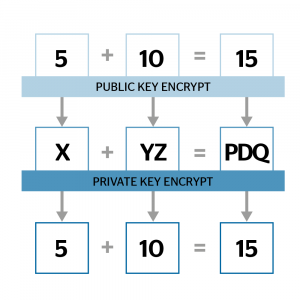
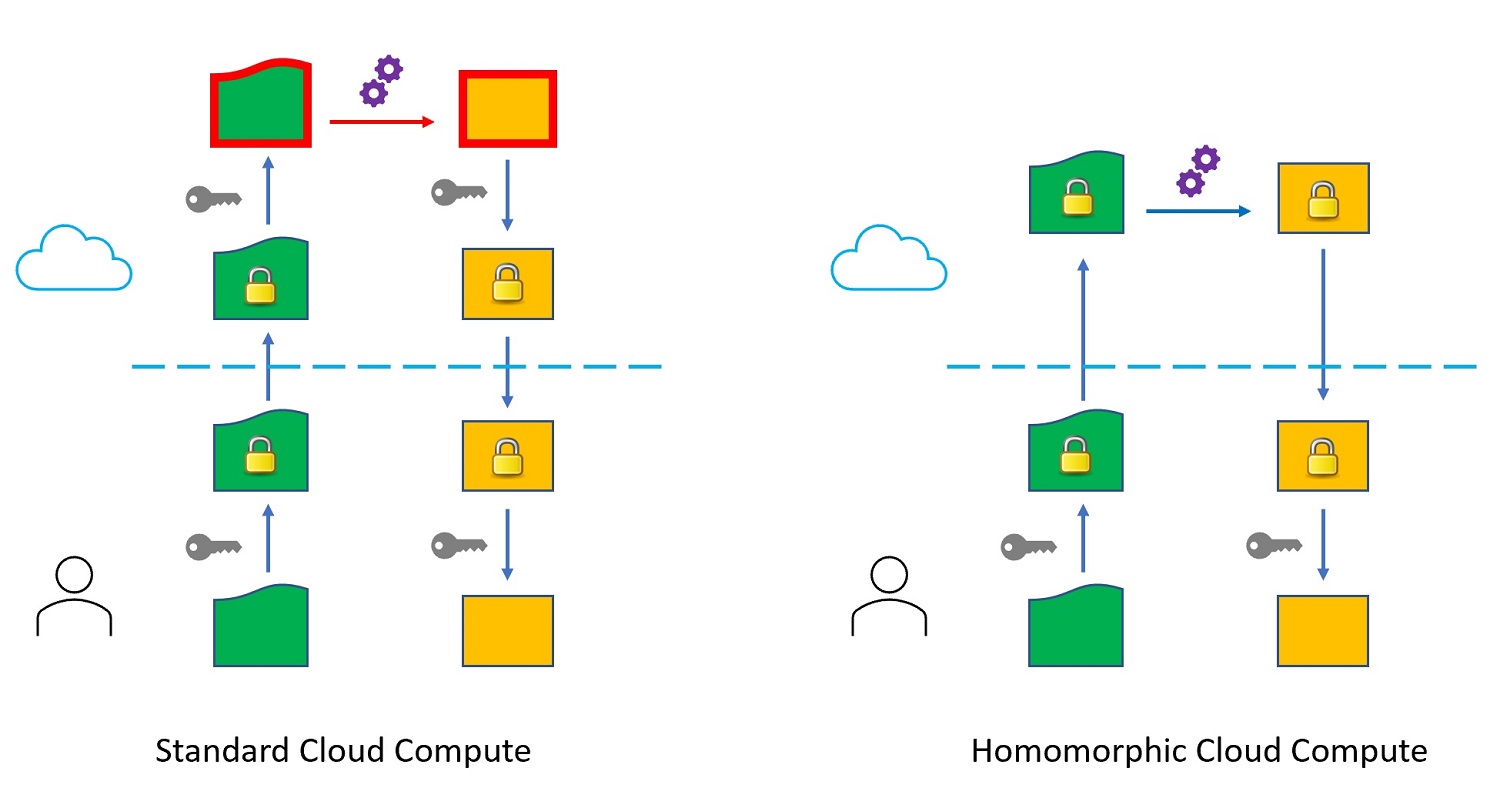
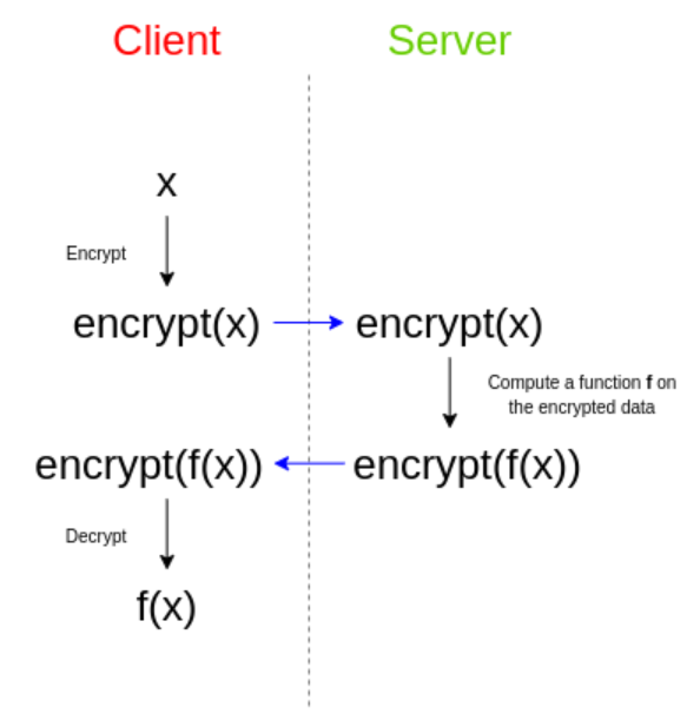
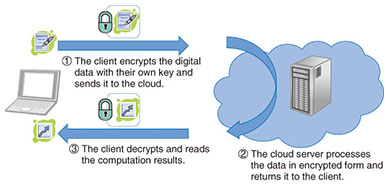
Is homomorphic encryption ready to deliver confidential cloud computing to enterprises? | TechRepublic
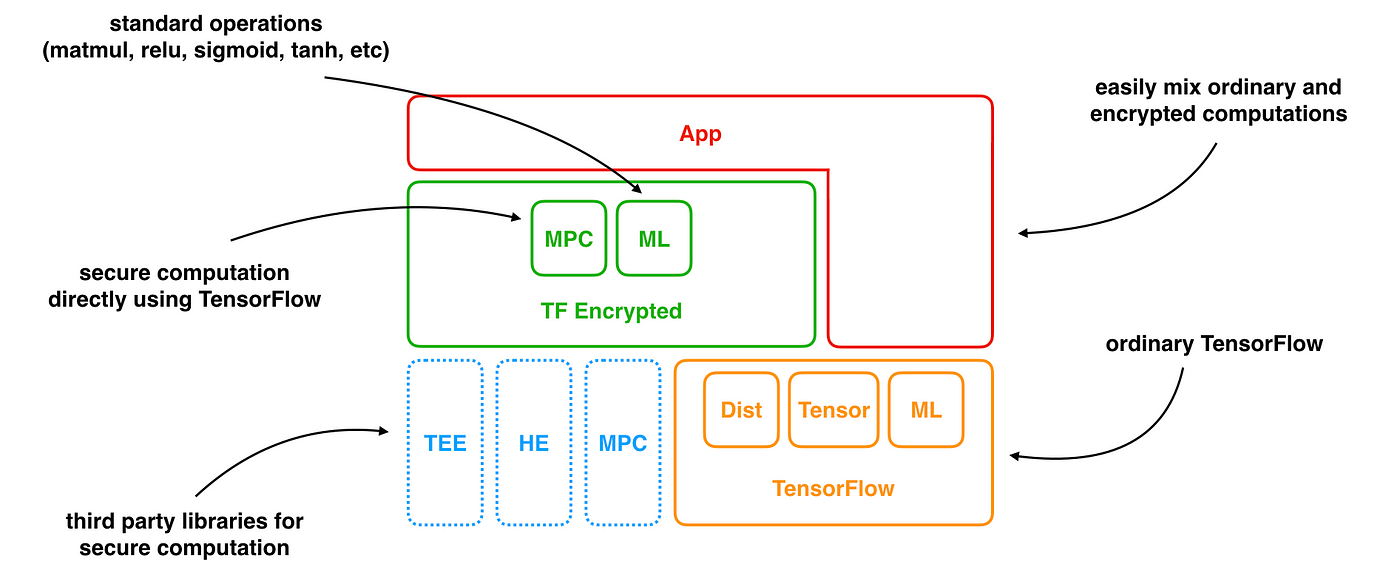
Growing TF Encrypted. And officially becoming a community… | by Morten Dahl | Cape Privacy (Formerly Dropout Labs) | Medium