Information Security Strategy Confidentiality Availability Integrity | Template Presentation | Sample of PPT Presentation | Presentation Background Images
Principle 2: The Three Security Goals Are Confidentiality, Integrity, and Availability | Information Security Principles of Success | Pearson IT Certification

National Computer Security Day is about everyday data privacy and client confidentiality - Guardian Data Destruction

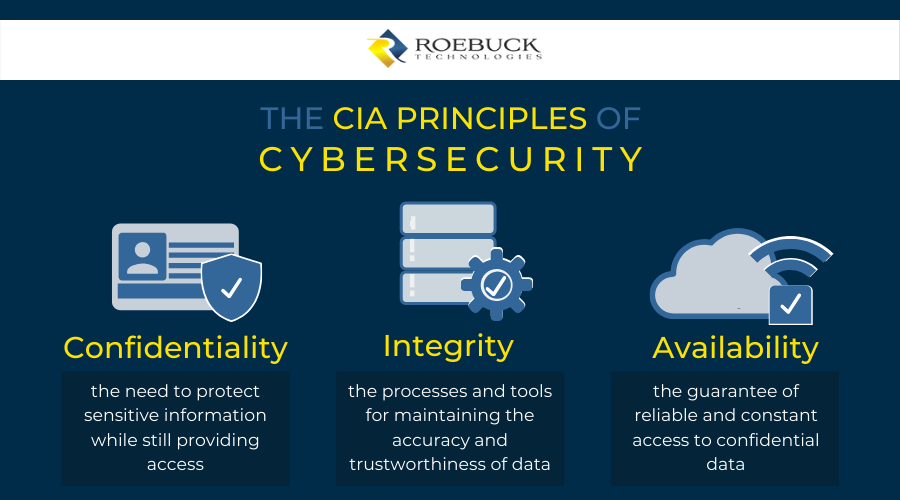
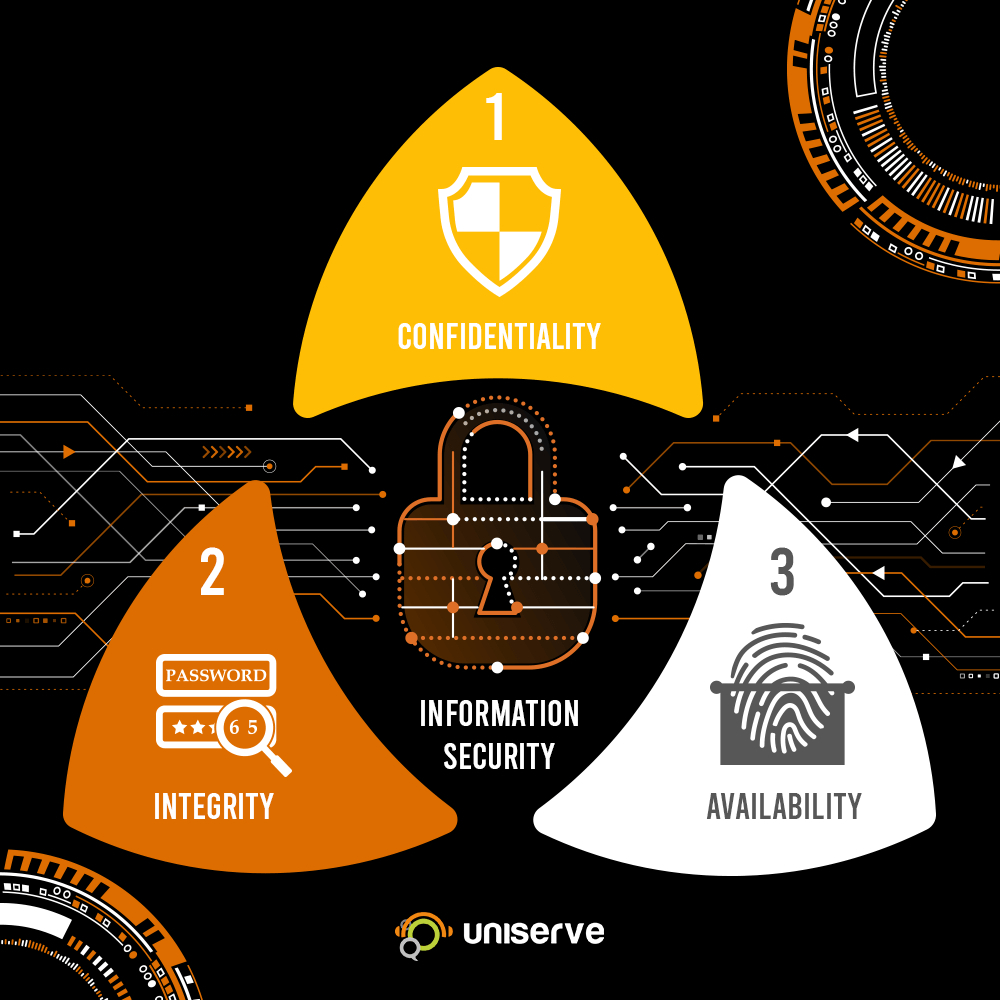
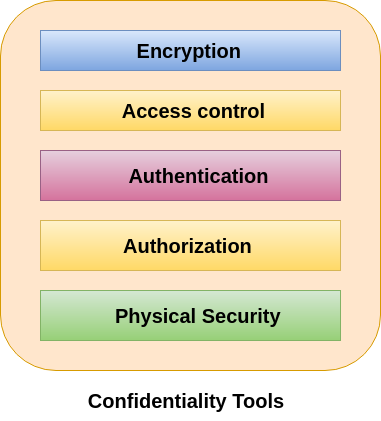
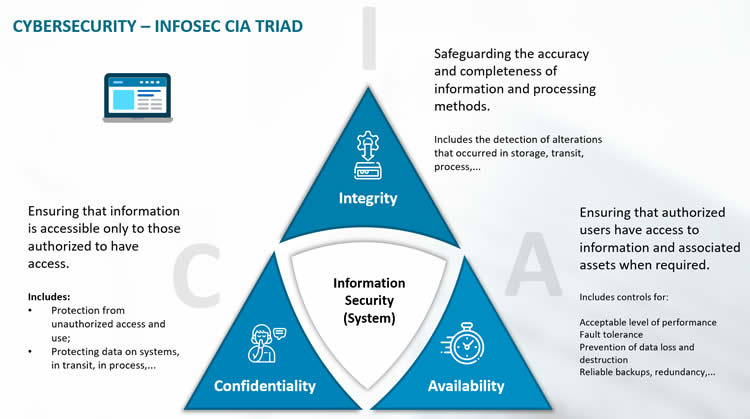
What Is the CIA Security Triad? Confidentiality, Integrity, Availability Explained – BMC Software | Blogs

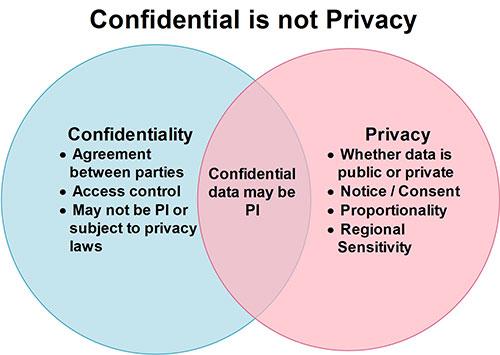

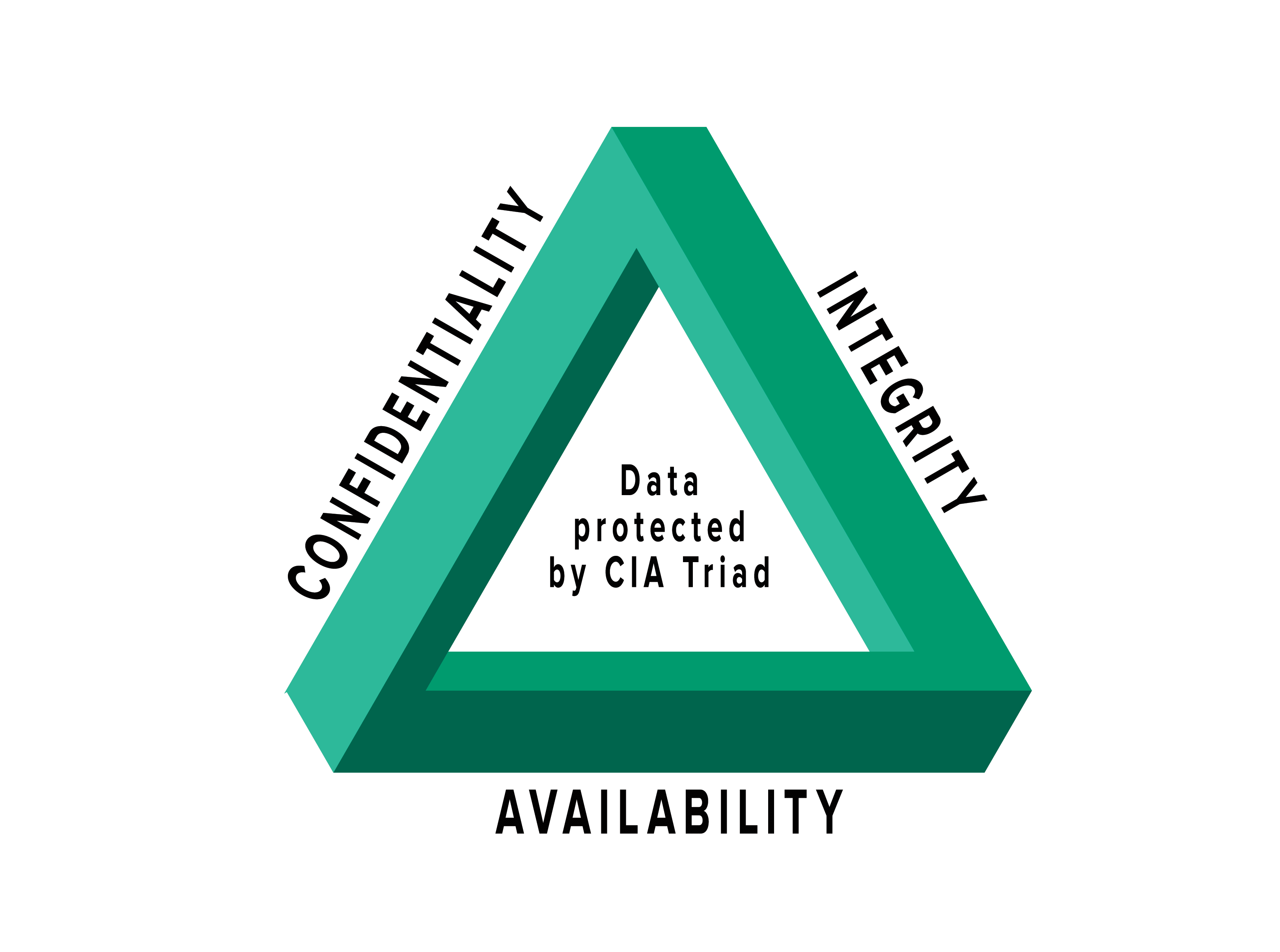


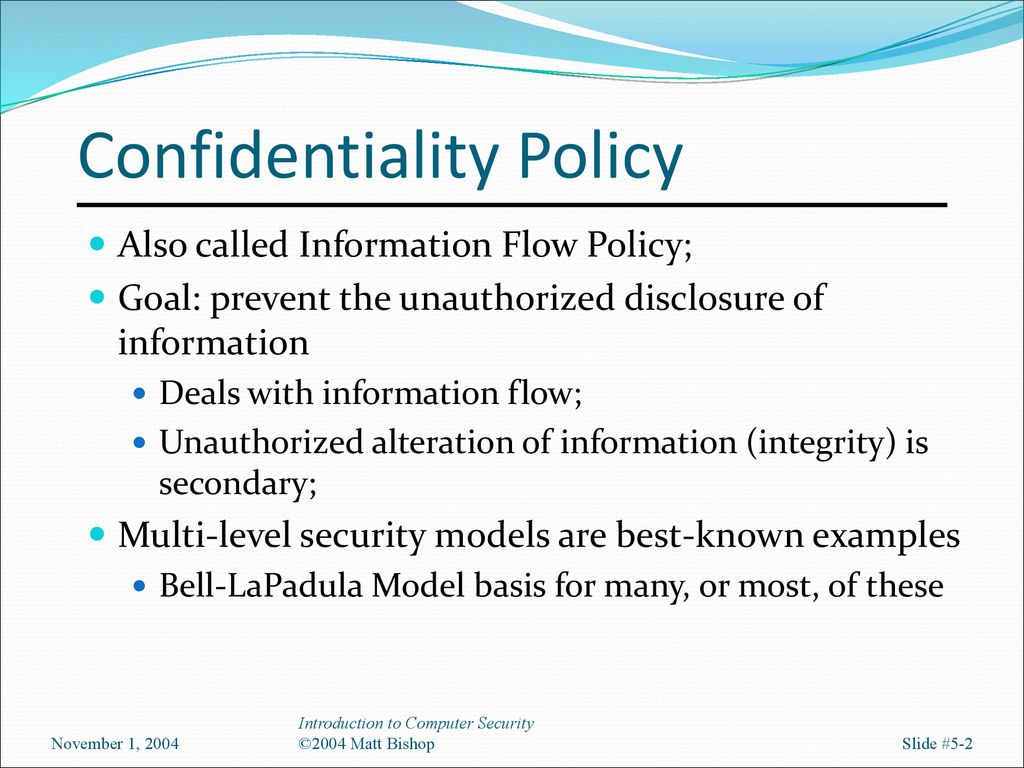
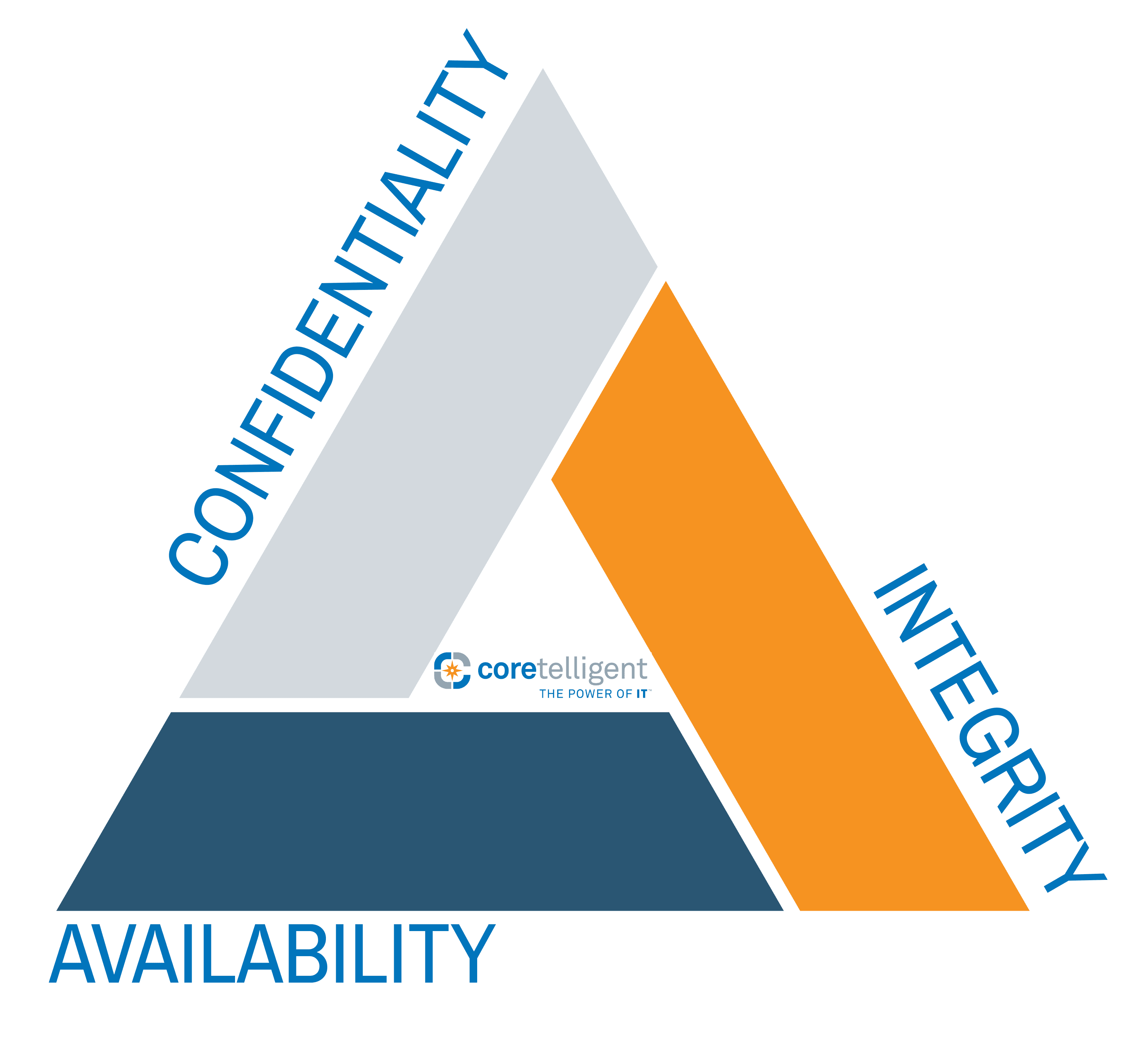

![Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager](https://dataprivacymanager.net/wp-content/uploads/2019/10/Three-pillars-of-information-security-and-cybersecurity.png)