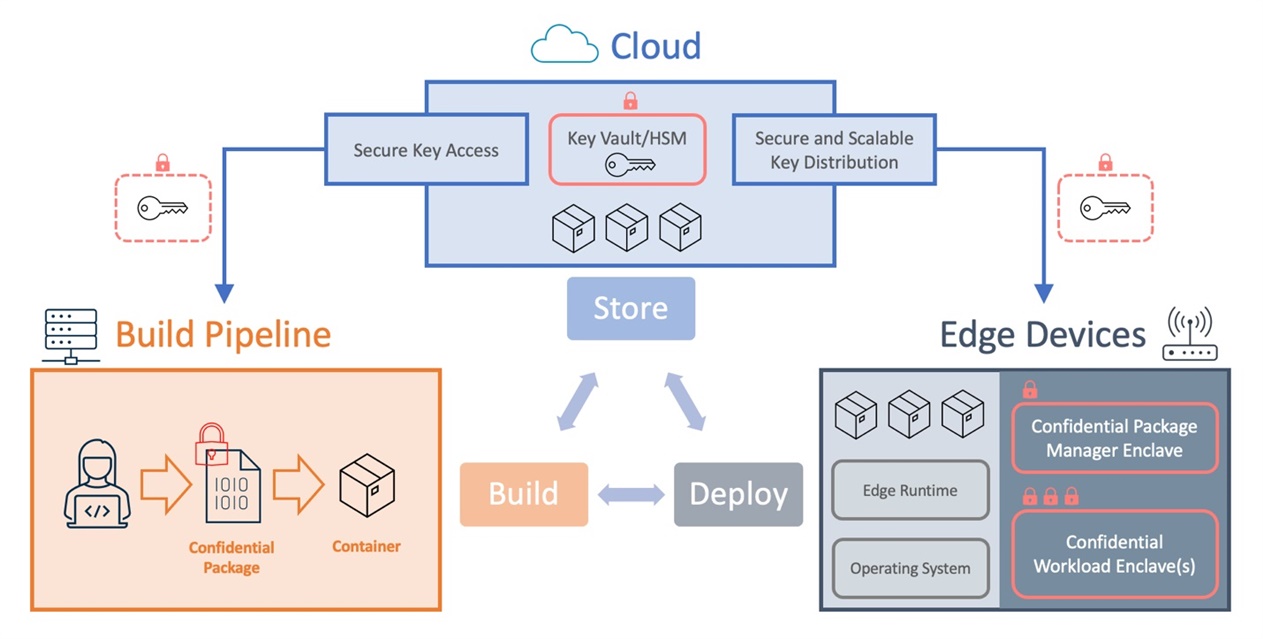
Confidential Computing Brings Secure Data Processing to the Edge - Infrastructure Solutions blog - Arm Community blogs - Arm Community
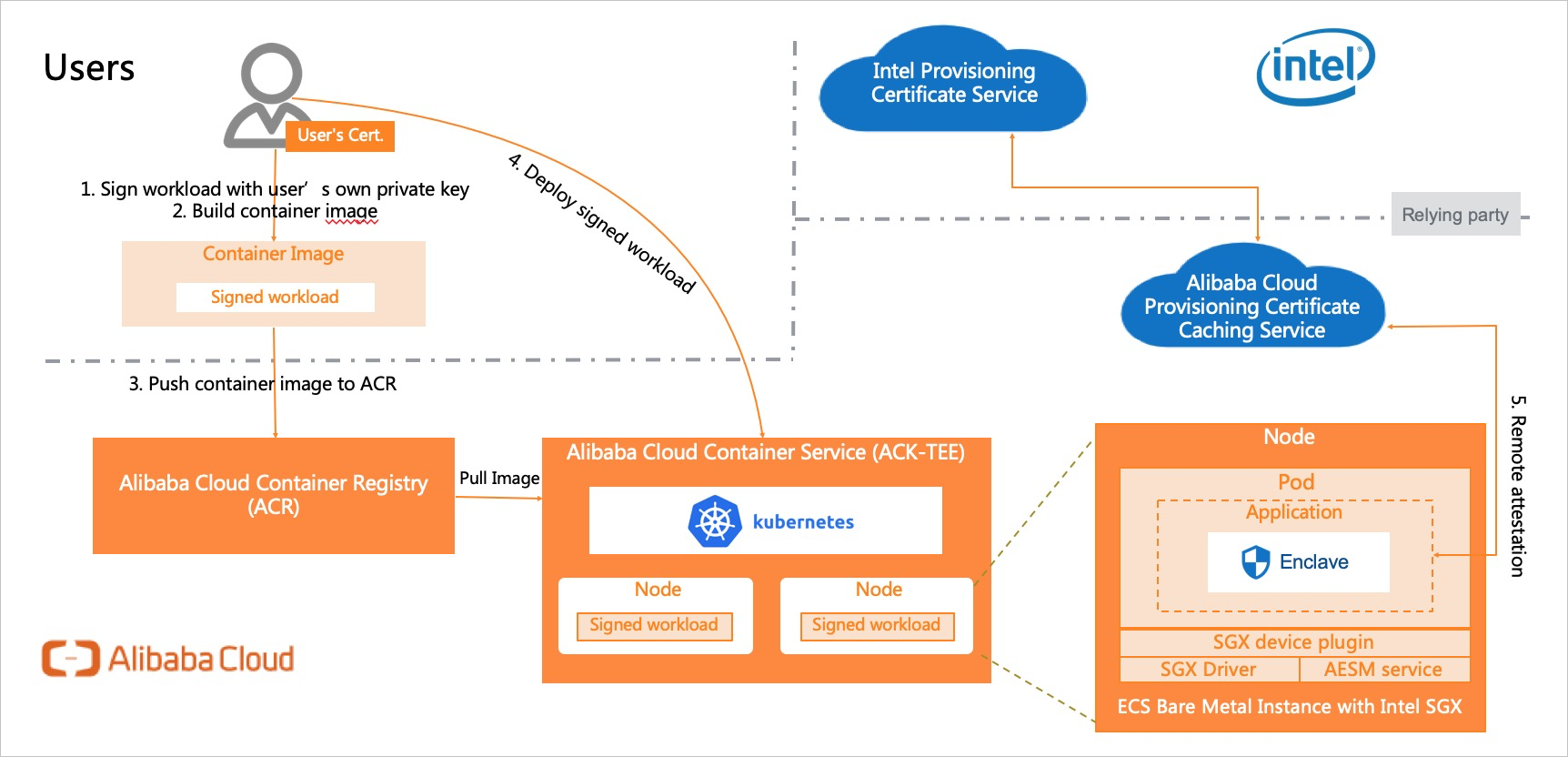
TEE-based confidential computing - Container Service for Kubernetes - Alibaba Cloud Documentation Center
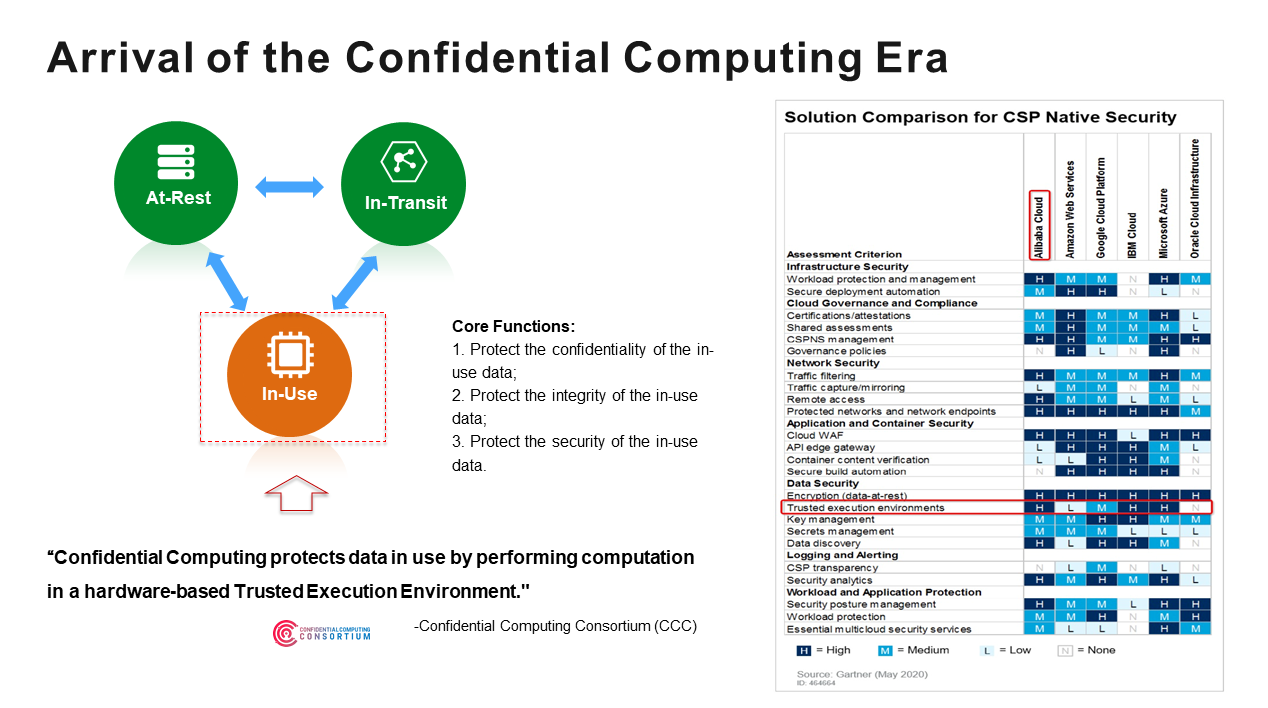




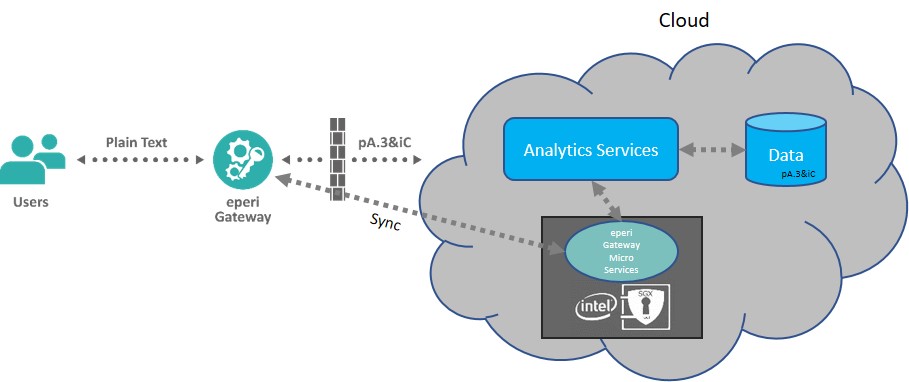

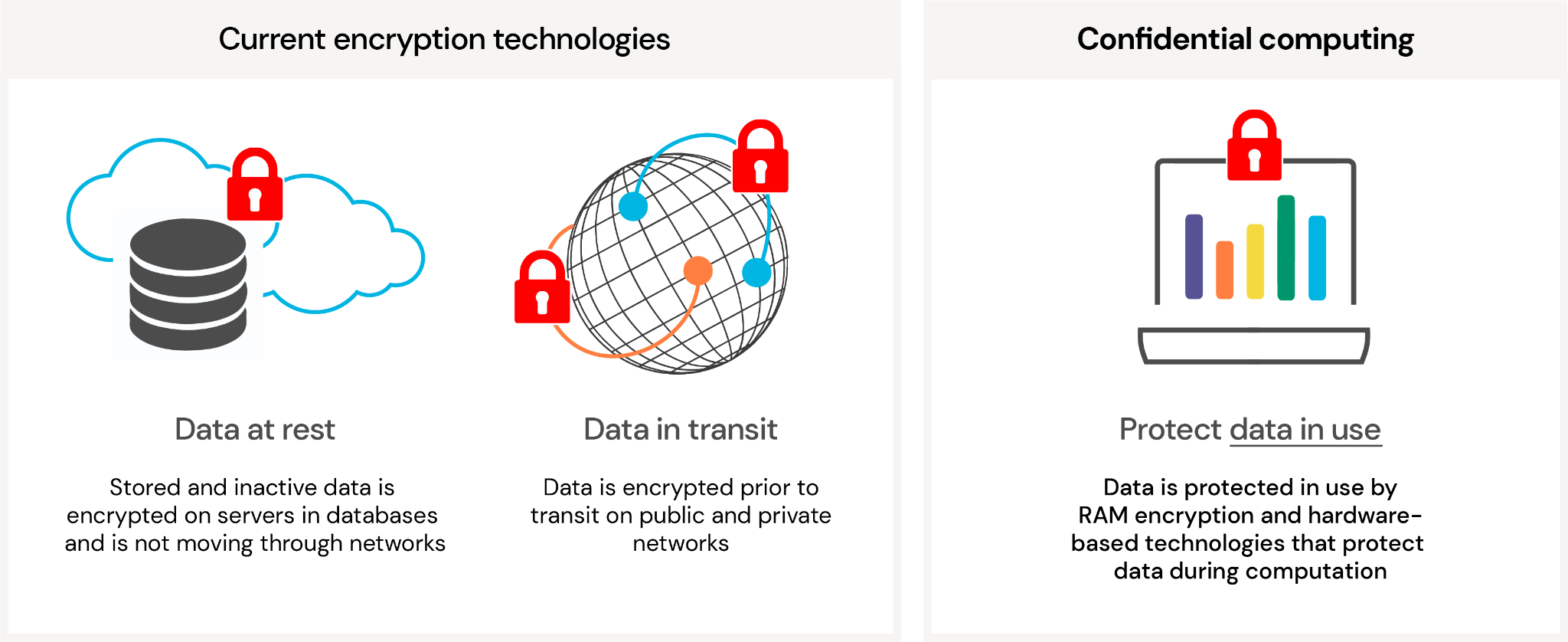

:quality(90)/p7i.vogel.de/wcms/78/5b/785bb8e02819ac1f5729f91818f97bca/0106915484.jpeg)
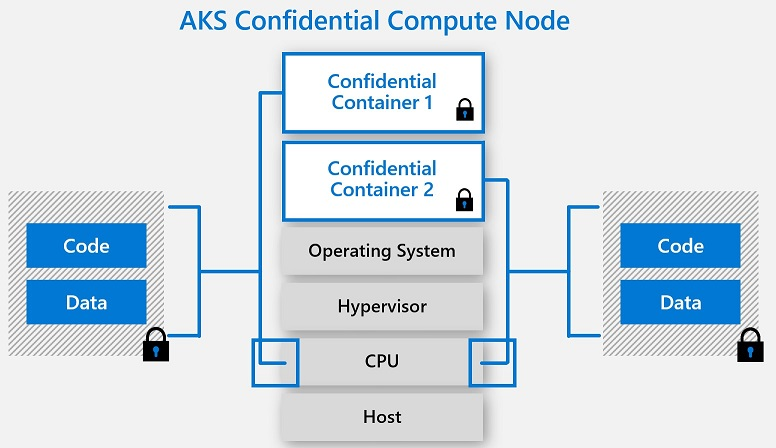


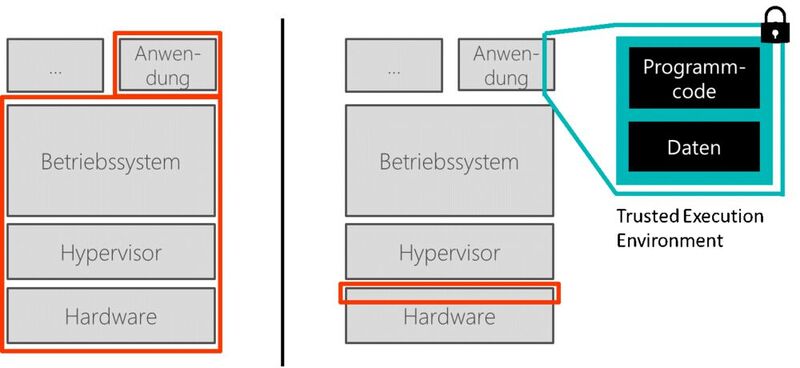







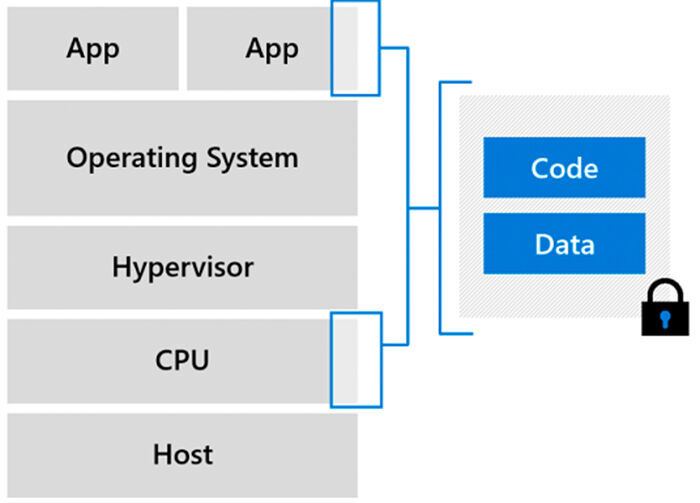
/filters:no_upscale()/news/2022/09/constellation-k8-confidential/en/resources/1edgeless-systems-constellation-1663880937405.jpg)