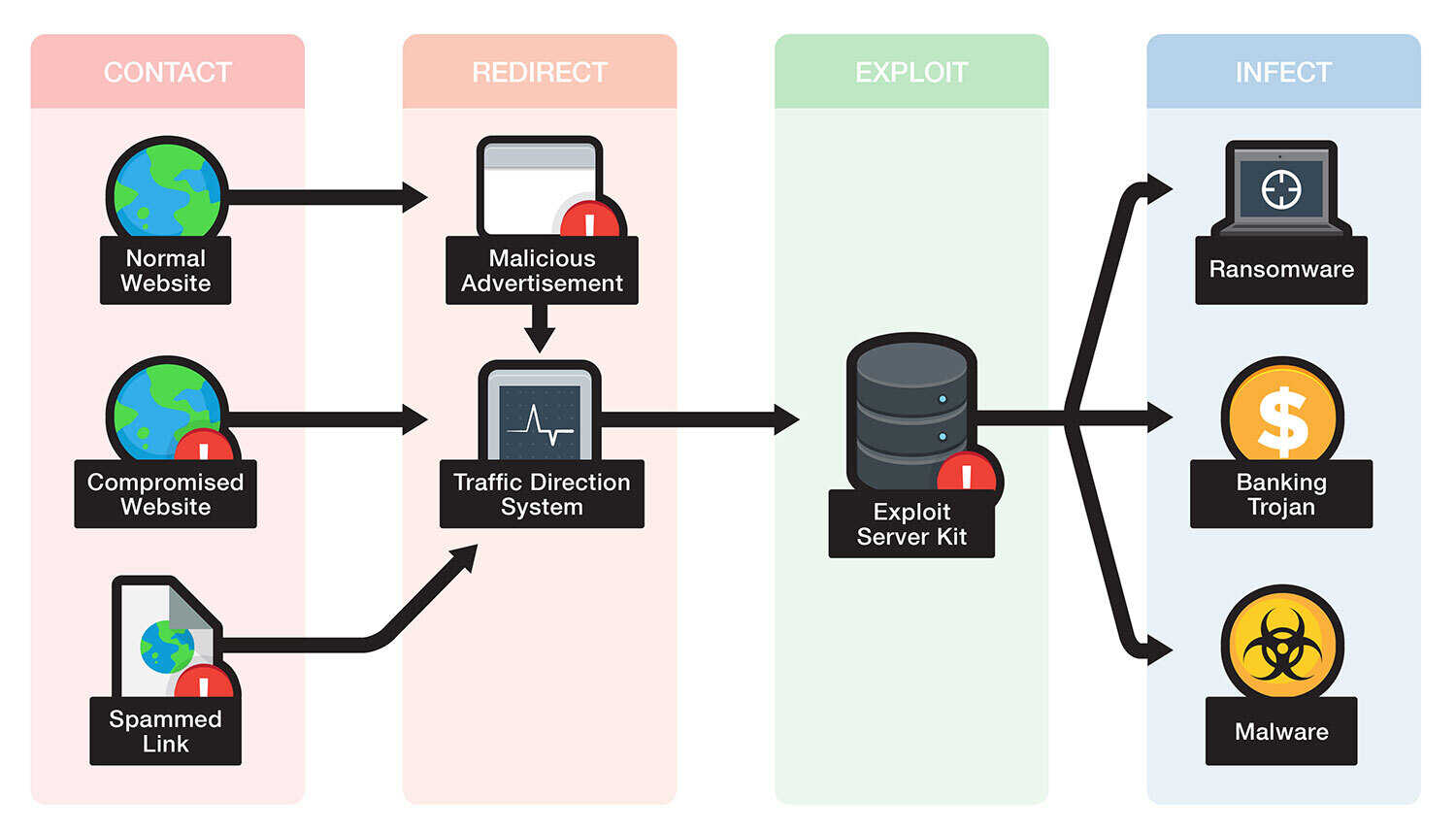
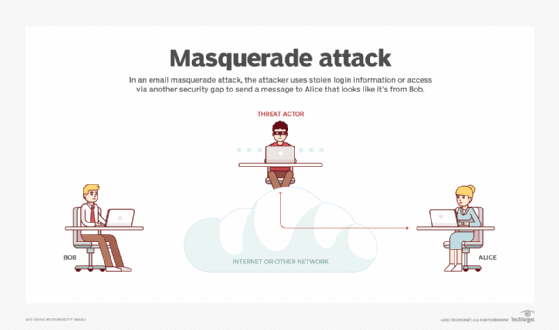
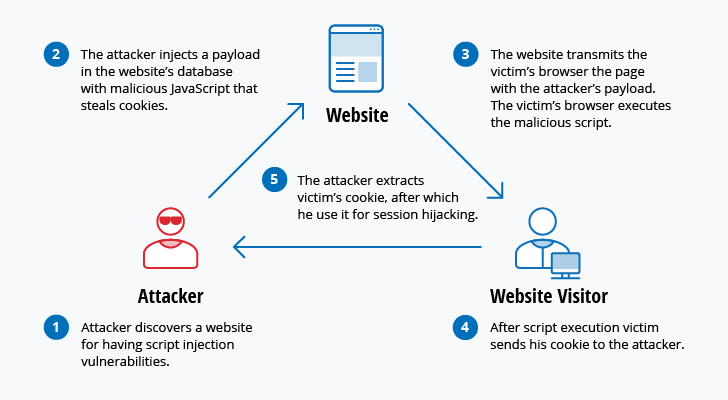
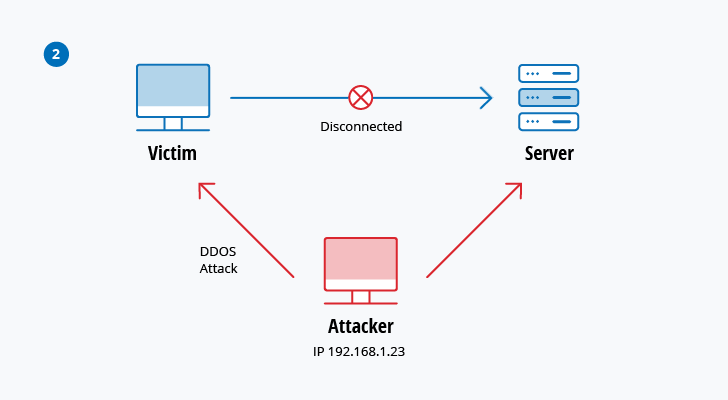
Gangstalking Survival. Who, how, & ways to expose on Twitter: "Hack The Hackers to Stalk the stalkers. Computer network exploitation (CNE) is a technique through which computer networks are used to infiltrate

A comprehensive review study of cyber-attacks and cyber security; Emerging trends and recent developments - ScienceDirect