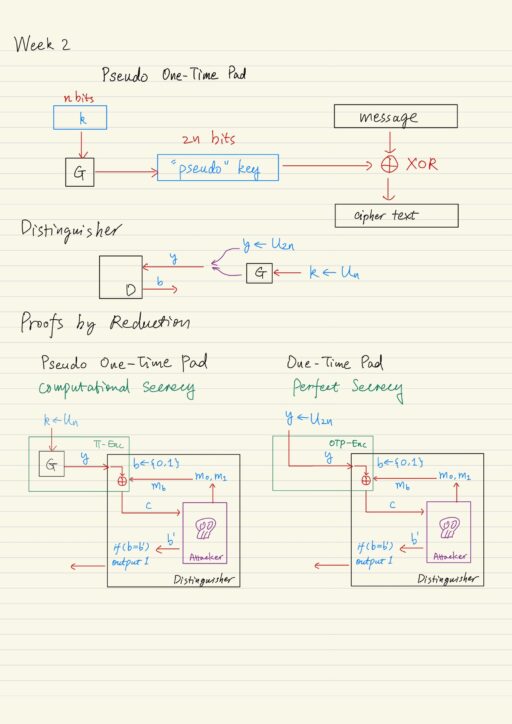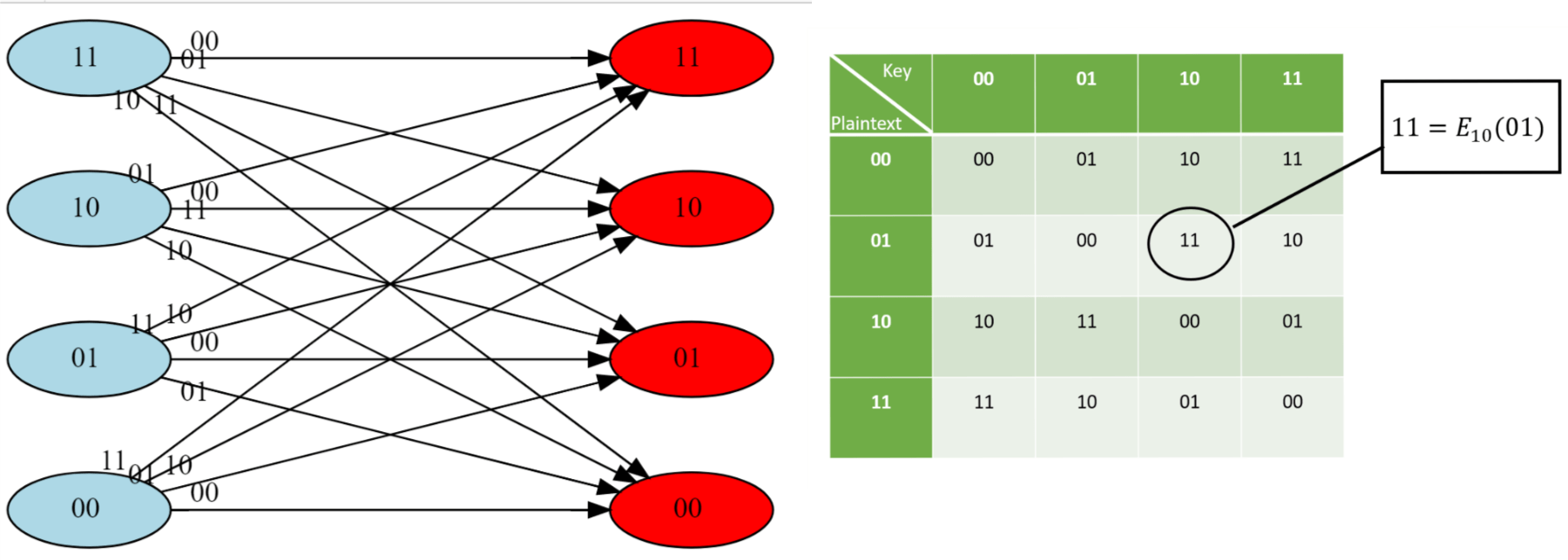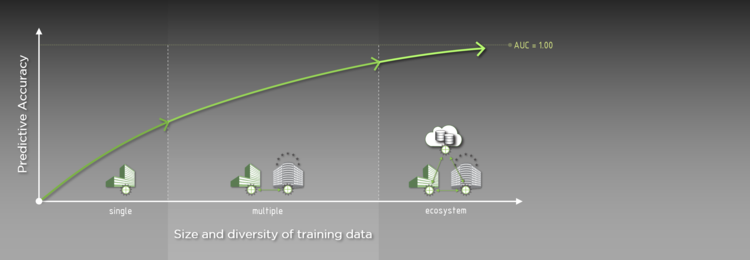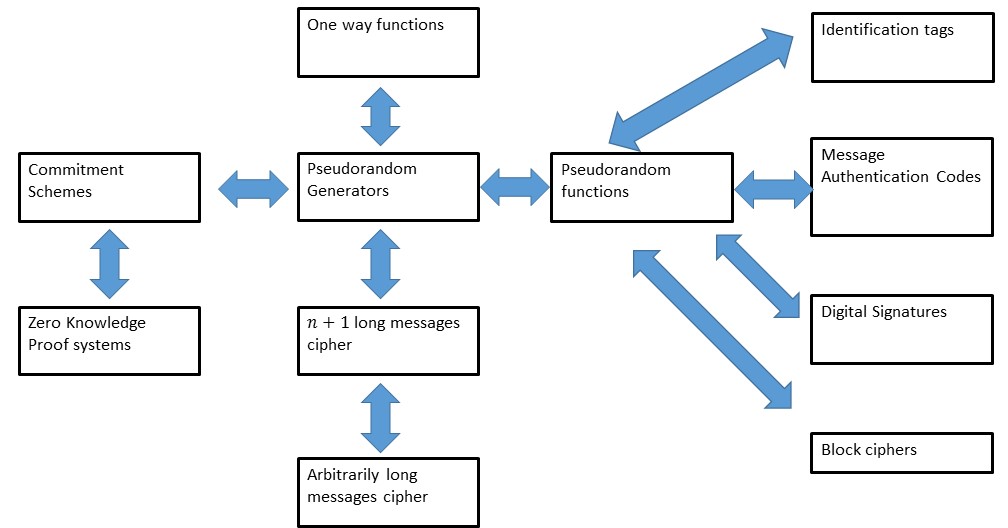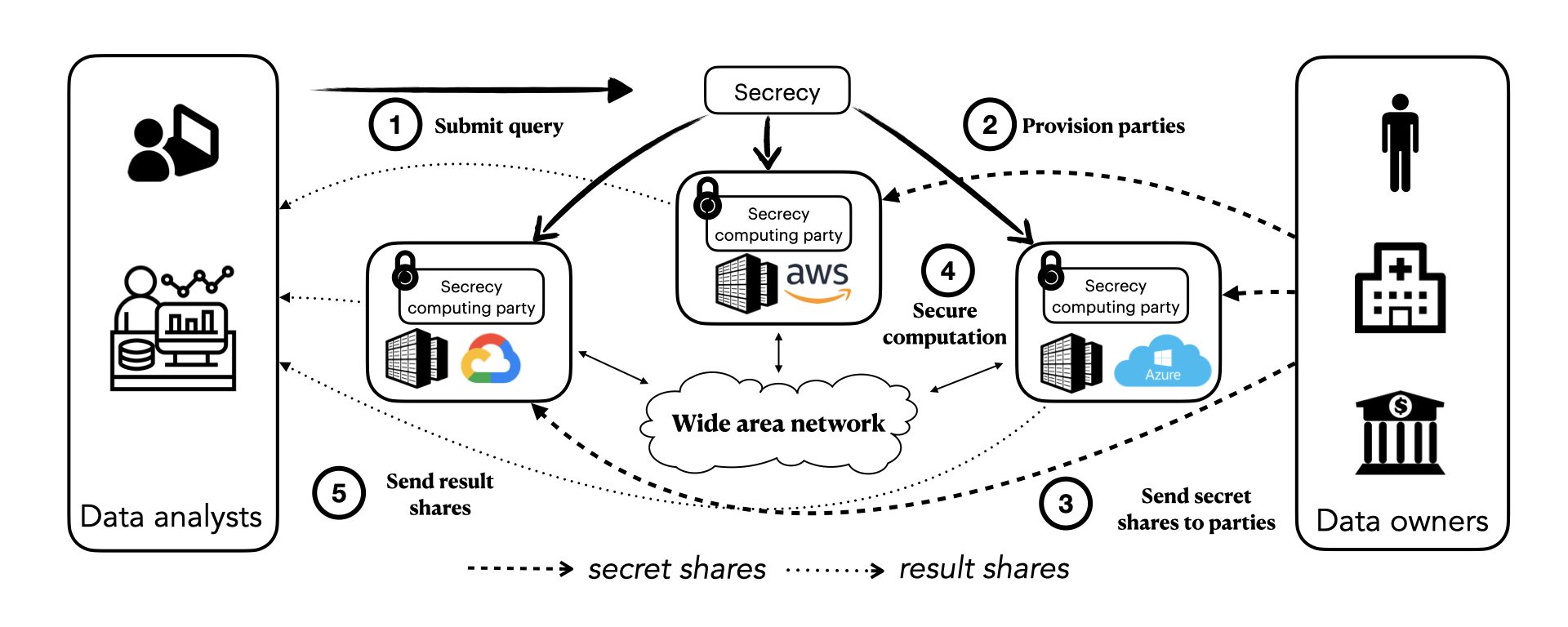
Secrecy: Secure collaborative analytics in untrusted clouds” accepted at NSDI'23 | Complex Analytics & Scalable Processing (CASP) Research Lab

What's the secret to a successful lab? New “About My Lab” Collection in PLOS Computational Biology - PLOS Biologue