
A Guide to Claims-Based Identity and Access Control, Second Edition – Book #ADFS #Office365 | Cloud and Datacenter Management Blog

A Guide to Claims-Based Identity and Access Control: Authentication and Authorization for Services and the Web (Microsoft patterns & practices) : Baier, Dominick, Bertocci, Vittorio, Brown, Keith, Densmore, Scott, Pace, Eugenio, Woloski,

Role-Based Access Control (RBAC) Authorization In Claims-Aware Applications and Services - TechNet Articles - United States (English) - TechNet Wiki

A Guide to Claims-Based Identity and Access Control: Authentication and Authorization for Services (Pre-Owned Paperback 9780735640597) by Dominick Baier, Vittorio Bertocci, Professor Keith Brown - Walmart.com

Role-based access control (RBAC) vs. Claims-based access control (CBAC) in ASP.NET MVC - Stack Overflow

A Guide to Claims-Based Identity and Access Control, Version 2 : Authentication and Authorization for Services and the Web by Vittorio Bertocci, Eugenio Pace, Dominick Baier, Keith Brown and Scott Densmore (2013,

The Enhanced Access Control Model to Encrypted Data based on an XACML... | Download Scientific Diagram

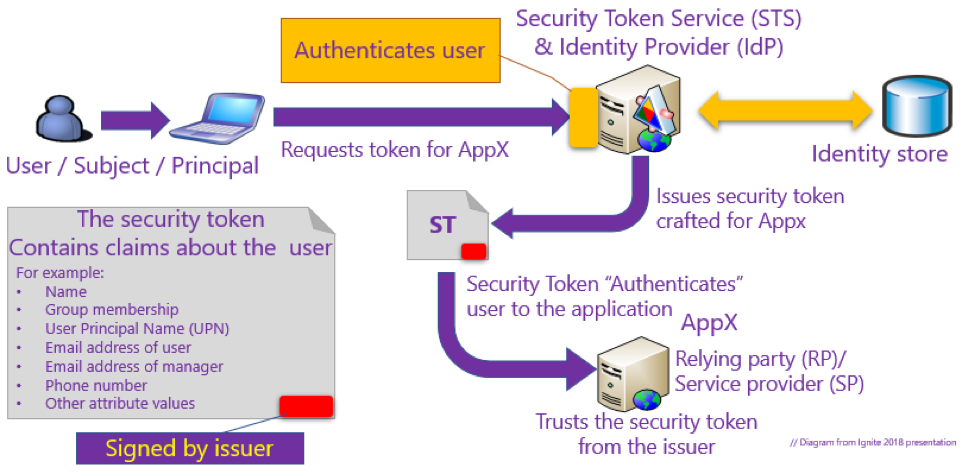

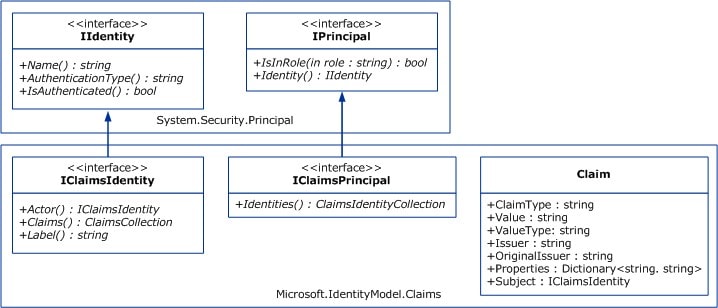


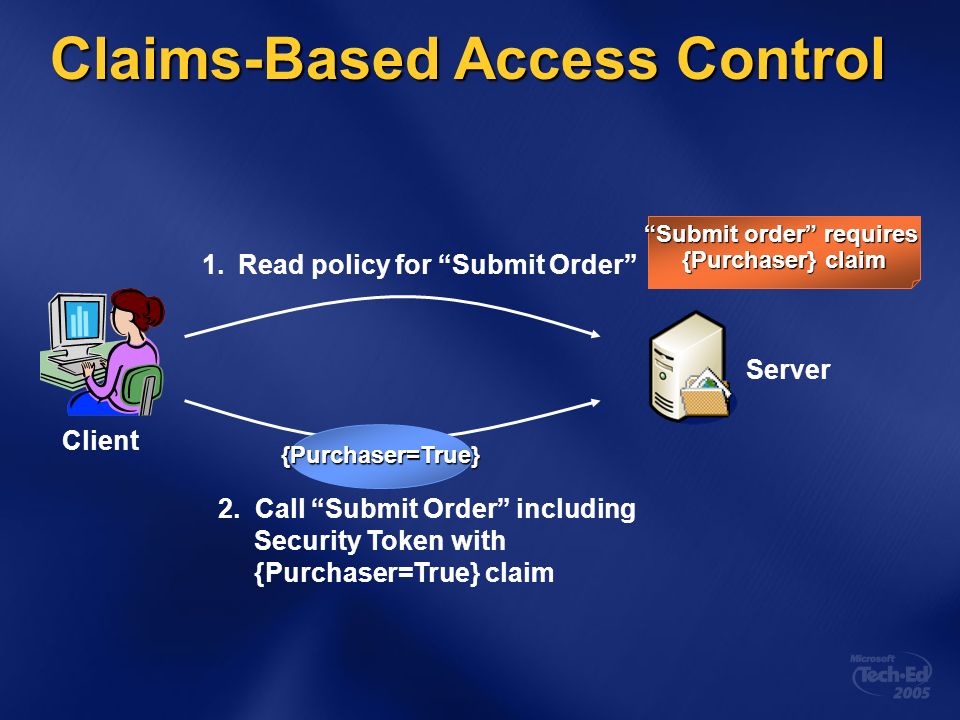
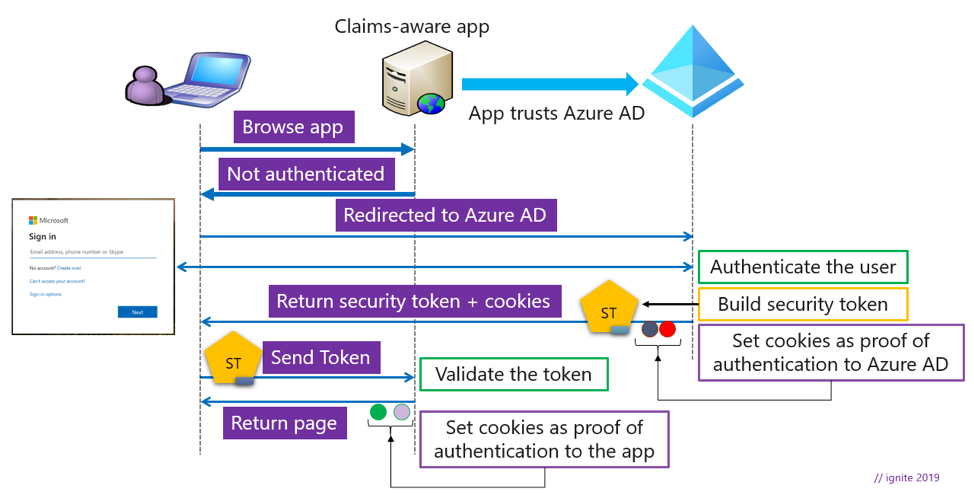

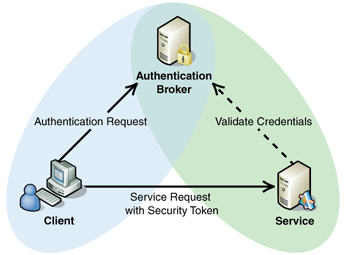

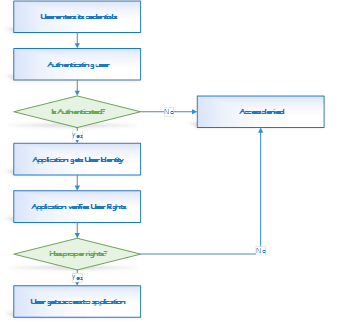
![PDF] Claims-Based Enterprise-Wide Access Control | Semantic Scholar PDF] Claims-Based Enterprise-Wide Access Control | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/59cb9924e2817ef35b1268b3f856c864b4d3c659/3-Figure2-1.png)




