More Than 98% of MSPs Operate Without Any Cybersecurity Certification. Why This Should Terrify You. - Strategic Technology Solutions

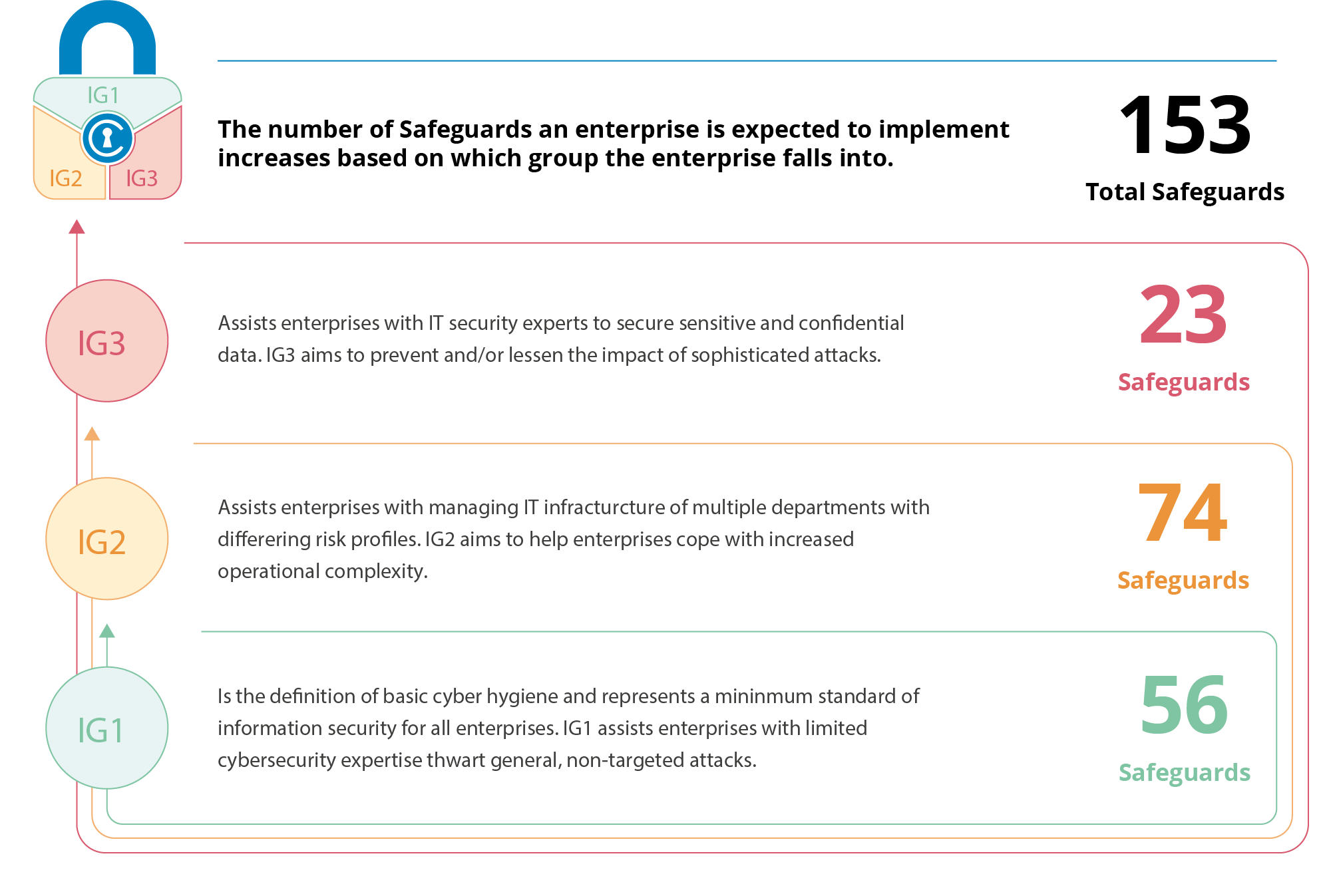
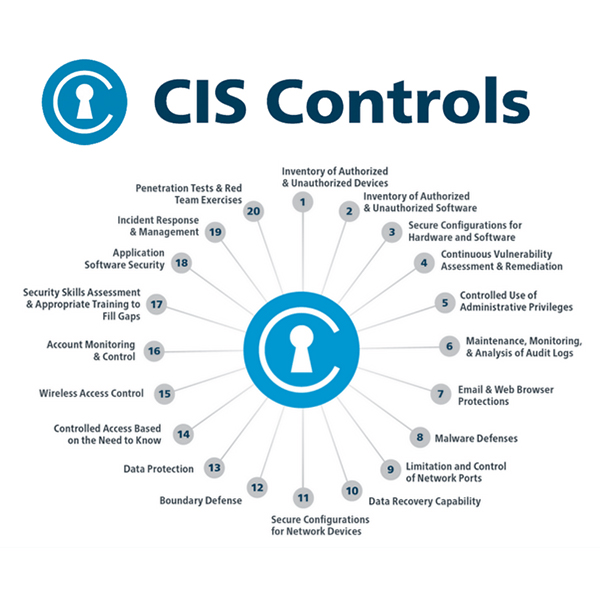
CIS Critical Security Controls – Six “Basic” Strategies to Deliver Immediate and Effective Cyber Defense - Valeo Networks

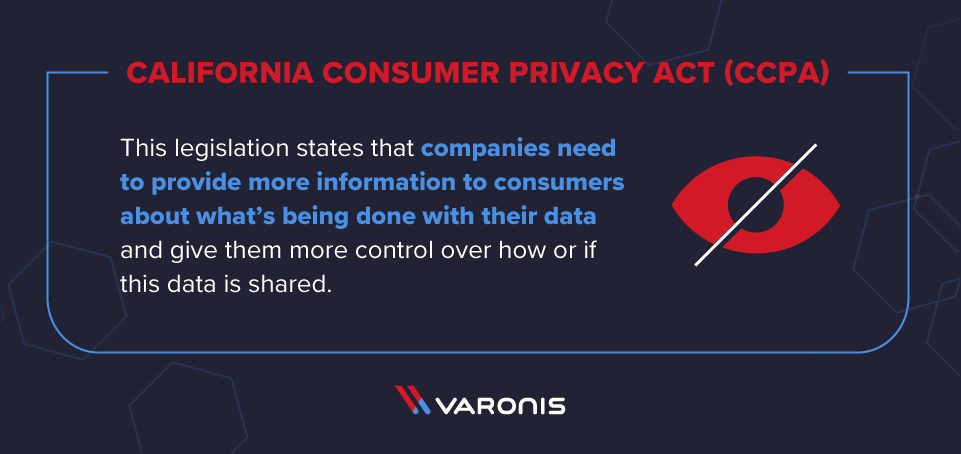
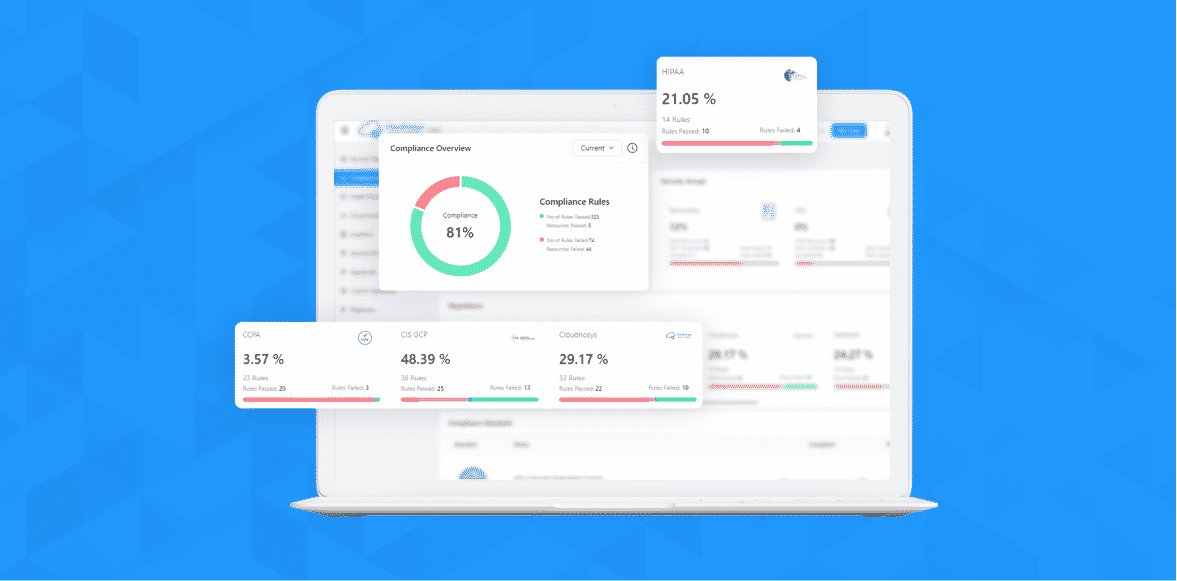
Expedite CIS Controls for California's CCPA and New York's SHIELD compliance with BigFix - HCL SW Blogs

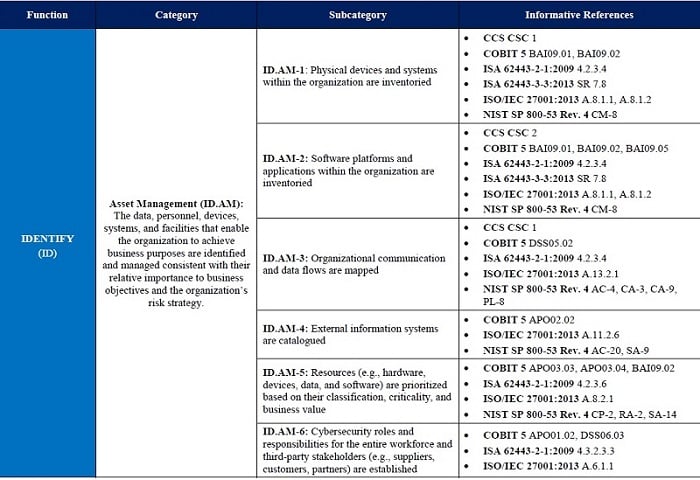
Cyber Security Best Practices: No. 1: Hardware Inventory | ITPro Today: IT News, How-Tos, Trends, Case Studies, Career Tips, More










.png)