GitHub - columbia/VIA: Mirror of Artifact for OSDI 22 Paper: Design and Verification of the Arm Confidential Compute Architecture

Arm CCA Confidential Computing: Arm Builds Data Center Secure Enclaves | Data Center Knowledge | News and analysis for the data center industry

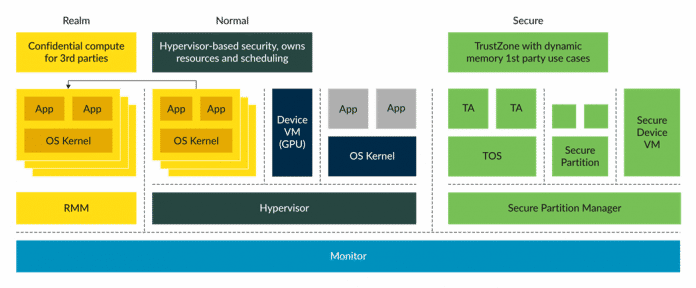
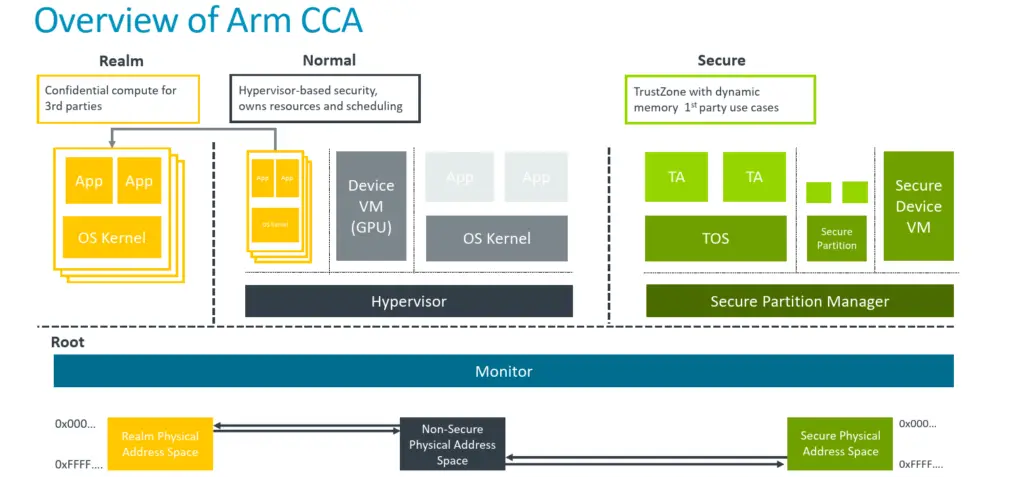
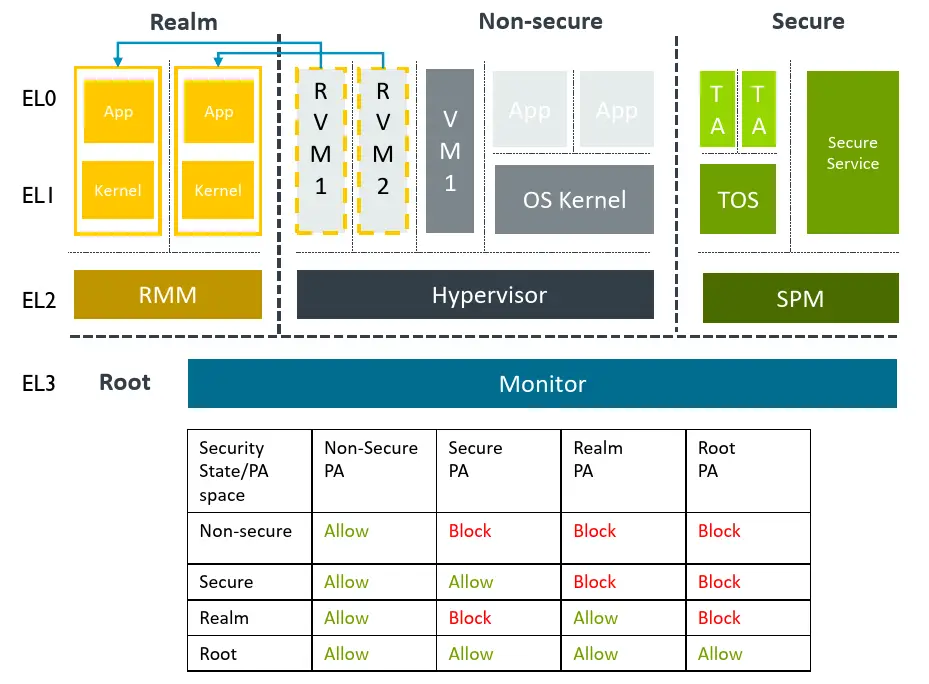
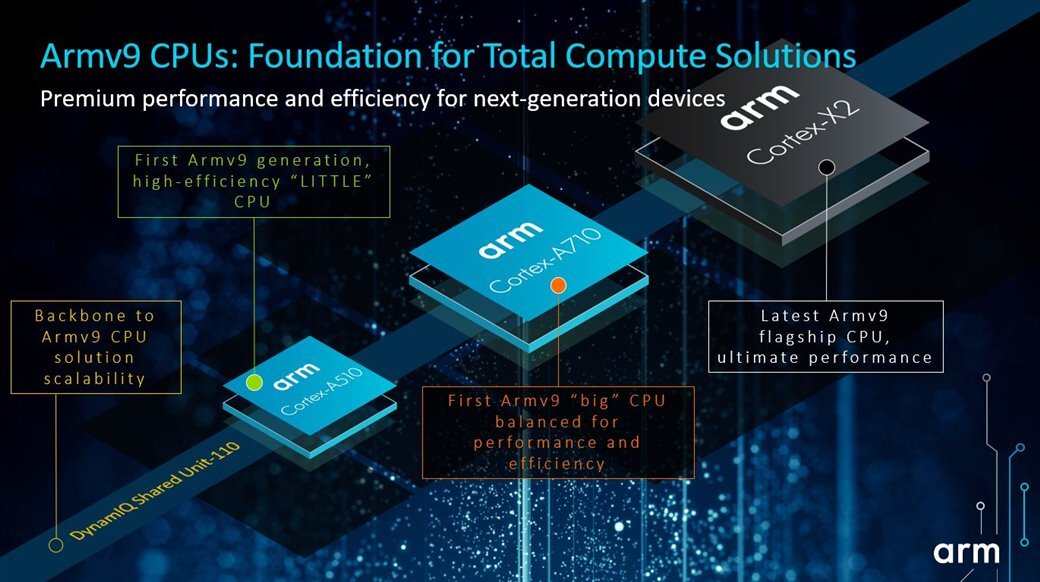
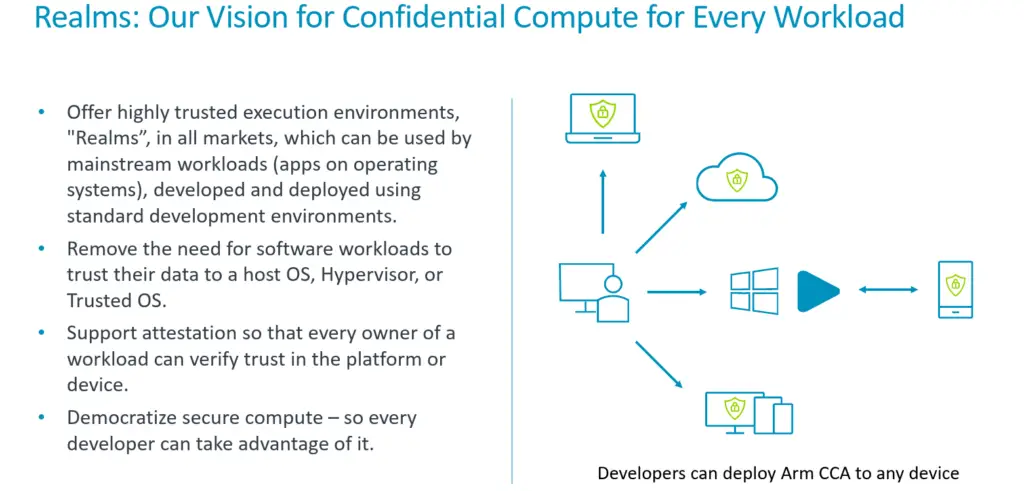
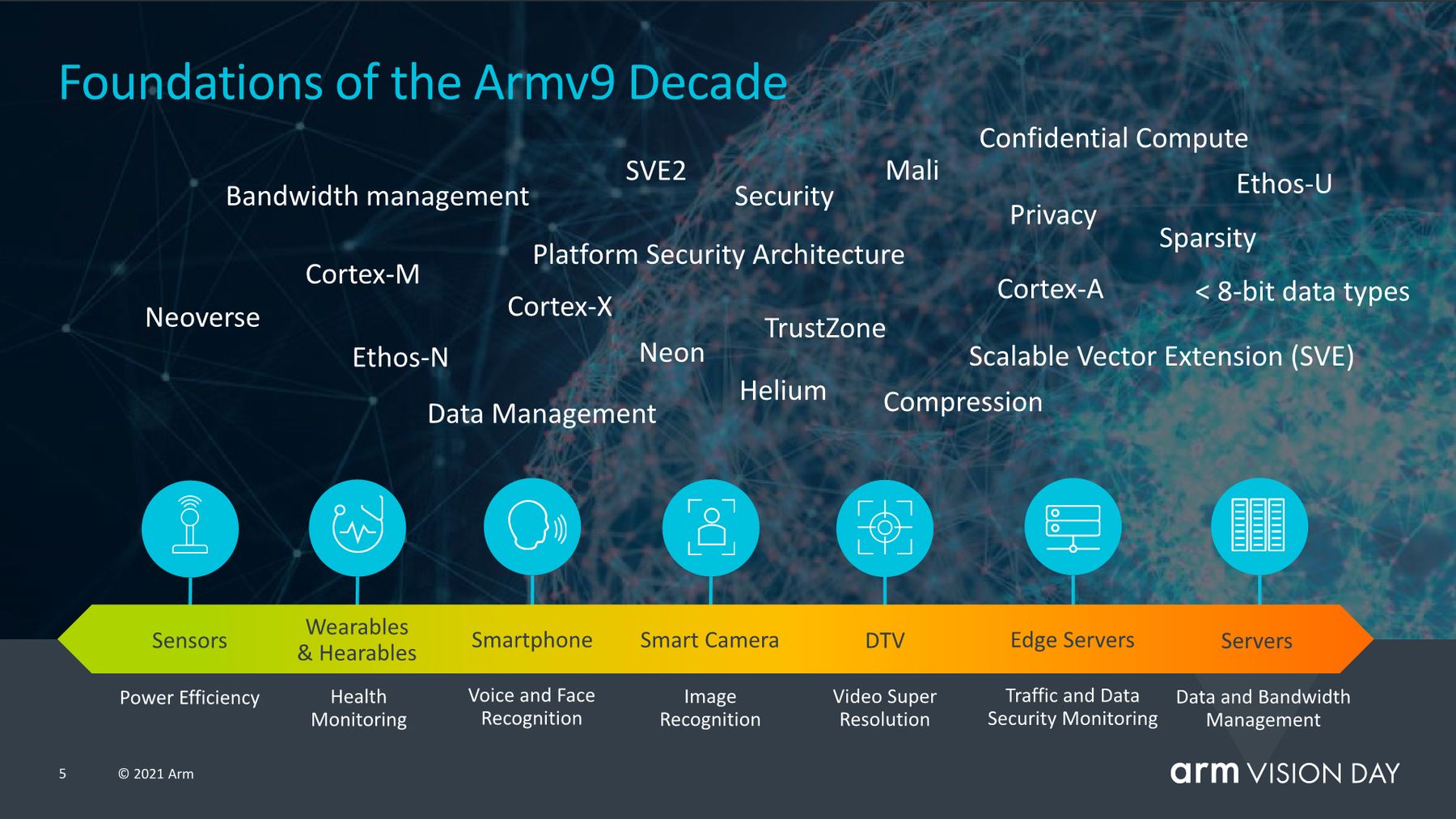
Introducing the Confidential Compute Architecture - Arm Announces Armv9 Architecture: SVE2, Security, and the Next Decade

Introducing the Confidential Compute Architecture - Arm Announces Armv9 Architecture: SVE2, Security, and the Next Decade

Introducing the Confidential Compute Architecture - Arm Announces Armv9 Architecture: SVE2, Security, and the Next Decade
Apple's Dedication to Protecting Privacy will be aided by Arm's next-Gen ARMv9 Architecture feature known as 'Confidential Compute' - Patently Apple