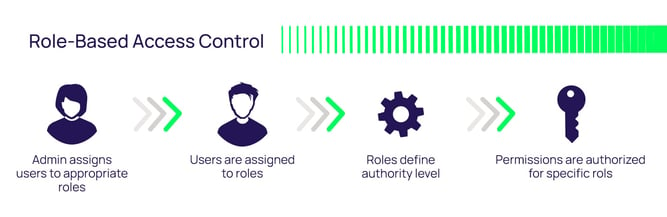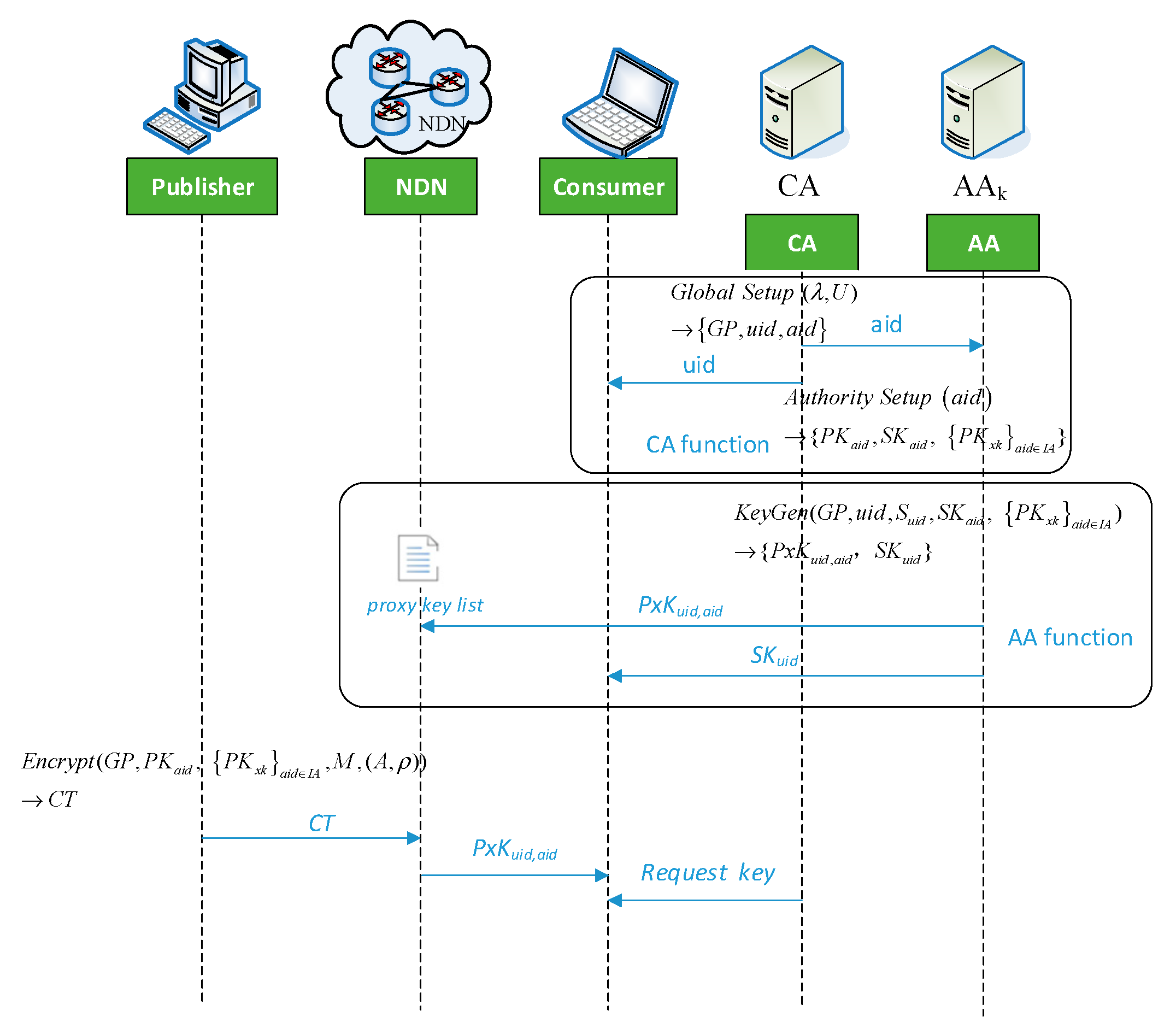
Future Internet | Free Full-Text | Multi-Authority Revocable Access Control Method Based on CP-ABE in NDN

1 Access Control Systems & Methodology. Access control is the collection of mechanisms that permits managers of a system to exercise a directing or restraining. - ppt download

Authentication and Access Control: Practical Cryptography Methods and Tools : Boonkrong, Sirapat: Amazon.de: Bücher

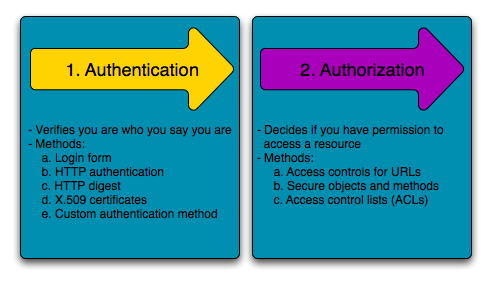








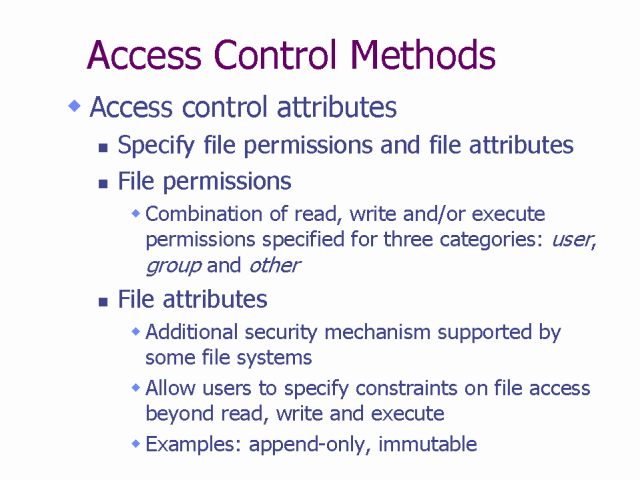
![PDF] Methods for Access Control : Advances and Limitations | Semantic Scholar PDF] Methods for Access Control : Advances and Limitations | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6192f0308dc8d7782b55a0557dfb66f323638853/4-Figure1-1.png)